
Layered Defenses at BSides Seattle
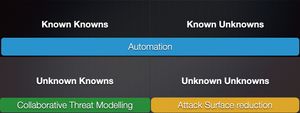
How do we use models to help us answer what are we going to do?

How do we use models to help us answer what are we going to do?

Learn more about threat modeling and the Four Question Framework

Adam will be the featured speaker at the ISC2 Seattle Chapter meeting in February.
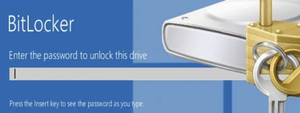
What can the Bitlocker story tell us about risk?
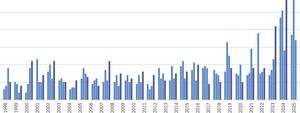
GPS attacks trigger revisiting threat models

In 2026, it’s more important than ever to take control of what you read
Congratulations to all involved!

Prompted by participants, a few closing thoughts for 2025
The first-ever, community-powered report on threat modeling

Get in, we’re rebooting the OWASP Threat Modeling project!

Two new versions of our “Publish your threat model” work are now available.

Read up on Adam's New Thing from October

Watch a masterclass in effective security processes

Understanding ‘prompt engineering’

What can the moon buggy teach us about modeling?

LLMs will change threat modeling. Will it be for the better?

Register for OWASP training in Washington D.C.!

Our biggest back to school sale of the year!

Everyone wants robots to help with threat models. How’s that working out?

A 2025 view of threat modeling tools
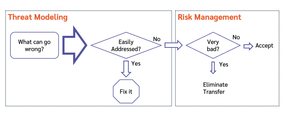
Threat modeling finds threats; risk management helps us deal with the tricky ones.

The CRA is coming and it's going to be a dramatic change for technology producers

Thinking of threat modeling with a knob helps you get more out of it.

What can we learn from Google’s approach to AI Agent Security

We think you should publish your threat model, and we’re publishing our arguments.

Automation sounds great, but what about the essence and beauty?

Free training for displaced government employees

Think like a what??!

What Andor can teach us about Information disclosure threats

Get one fourth off for May the fourth!

A great, in depth series on threat modeling with ATTACK

Pray they don’t alter the price any further
What's wrong with this process?

Grateful to introduce the Hackers' Almanack!

Register for OWASP training in Barcelona!

Clarifying how to threat model AI

Upcoming RSAC webinar

Adam was on the CyberTuesday podcast
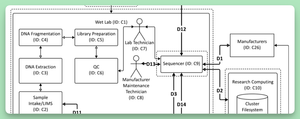
An exciting new sample TM from MITRE

The psychology of getting started threat modeling

Do diagrams leverage the brain in a different way?

Emerging research on Cyber Public Health


What should hackathon judges value?

Our latest whitepaper!

Our biggest black friday sale this year!
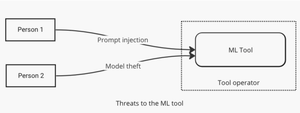
Why do we call them trust boundaries, anyway?

Our newest course: Scaling Threat Modeling

Threat model Thursday, let's dive deep into a detailed approach to using ATT&CK
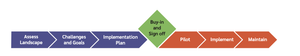
Scaling threat modeling can be a challenge!

Threatmodcon was amazing

Our biggest sale ever ends today!

Our biggest sale ever!

Office hours are one way we strive to deliver a great training experience.

My talk from ThreatModCon Lisbon 2024

How to effectively threat model authentication.

Authentication is more frustrating to your customers when you don’t threat model.

The early bird pricing for my Blackhat training expires this Friday
How can we think about non-standard symbols in threat modeling diagrams?

Adam on Enterprise Security Weekly podcast

How we leverage a platform for great training

Adam on Healthcare Info Security podcast
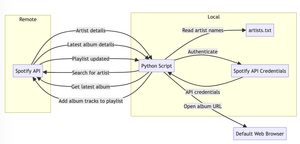
Exploring LLM-driven coding as I get ready for Archimedes

We have an awesome new white paper available!

Submit your papers for ThreatModCon 2024 now!

Adam on The Security Table podcast

Thoughts on my instructional journey - and what yours might be

Red Teaming by Bryce Hoffman is a thought-provoking read.
A great new resource for threat modeling

(no description available)
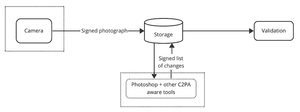
What can we learn from the C2PA security considerations document?

September was a big month in appsec for both memory safety and policy

Seats are available in our October training

Our feedback to CISA is now public

Some diagrams to help clarify machine learning threats

Cumulus is a cloud-oriented version of Elevation of Privilege
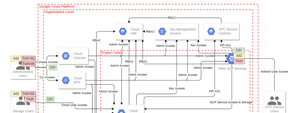
NCC has released a threat model for Google Cloud Platform. What can it teach us?

The threats book is in the supply chain, inconsistently.

The live launch party for Threats!

The serious side of the book

Like the Force, each threat has a light side, and a dark side.

Threat Modeling is the software version of measure twice, cut once.

External changes will be driving appsec in 2023. It’s time to frame the decisions in front of you.

A new paper on how fast, cheap and good can combine into something we usually discount.

More thoughts about AI and threat modeling

Pointer to Adam’s latest Darkreading article
Threat Modeling for UX Designers with Adam Shostack on Heidi Trost's podcast
Threats is almost in bookstores
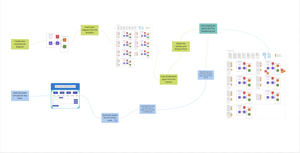
A Miro template for Elevation of Privilege

Oh my gosh, the boot camps are back!

Our next open course is in just a few weeks!

Our fall course offerings
So excited to share the cover with you

Threat modeling doesn't need to be big and complex

Adam joined Matt Tesauro on the OWASP podcast
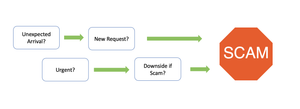
Roger Grimes has an exciting new model of scams that's going to transform how we teach people ot defend against them.

You don’t have to be technical, but you can’t make informed decisions about your business without threat modeling.

Using games to help us explore engineering techniques
Understanding how to choose the right threat modeling training can give you the education you want for the skills you need.

Adam on #WeHackPurple podcast

Holy cow, we’ve added new cards to Elevation of Privilege!
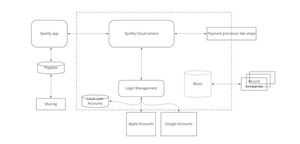
Open threat modeling training, Q1 2022

Threat modeling doesn't need to be a slow, heavyweight activity!

How to threat model medical devices? The FDA has released a playbook!
An important webinar by MDIC about the medical device threat modeling playbook is now available!
A video interview by OWASP leader Vandana Verma, on the topic of breaking into threat modeling.

Tremendous training opportunities in threat modeling and other topics at Appsec Global 2021
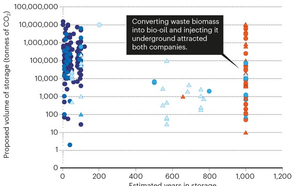
What happened when Microsoft tried to buy climate abatements

We learn while we're having fun. Some takeaways from a recent play to learn session.

New at Darkreading, a post on NIST and threat modeling

The World's Shortest Threat Modeling Video series continues with .. what can go wrong?

Are you tired of escalations and fights after pen tests find crucial security issues at the last minute? I have a discount code for upcoming threat modeling training that can help!
Let me call your attention to a new post by Irene Michlin, “Where Threat Modelling fits in the matrix?” (with a few comments on why it matters).

Are you tired of escalations and fights after pen tests find crucial security issues at the last minute? I have upcoming threat modeling training that can help!
Many people want their threat modeling work to produce risk numbers, and in this post you'll learn why that's a mistake.

Earlier this week, NIST released a Recommended Minimum Standard for Vendor or Developer Verification of Code. I want to talk about the technical standard overall, the threat modeling component, and the what the standard means now and in the future.
It's the latest in the World's Shortest Threat Modeling videos!
The latest in the World's Shortest Threat Modeling Videos.

At Blackhat USA, I'll be teaching Applied Threat Modeling.
The second video in my 60 second series!
I'm exploring the concept of very fast threat modeling videos.

You know what's not in my threat model? A meteor hitting a volcano... And that's ok!

Threat model Thursday is not just back, but live again!
Apple has released ‘Device and Data Access when Personal Safety is At Risk’ and I wanted to explore it a bit.
Expanding on the UK Government's ‘The Uk Code of Practice for Consumer IoT Security’ and how it aligns with Threat Modeling.

I get this question a lot: Can distributed/remote training work as well as in person? Especially for threat modeling, where there's a strong expectation that training involves whiteboards...

Developing a training program is hard, especially when it will be delivered remotely.

Through the pandemic, I’ve rebuilt the way I teach threat modeling. The new structure and the platforms I needed to adapt for my corporate clients also allows me to offer the courses to the public.

Bringing threat modeling to more and more people, now through a series of courses on LinkedIn.

Effective Threat Modeling by itself can ensure that your OKRs and AppSec Program are not only in great tactical shape, but also help define a strategic roadmap for your AppSec Program.
For Data Breach Today, I spoke with Anna Delaney about threat modeling for issues that are in the news right now.

Dr. Gary McGraw joins the IriusRisk Technical Advisory Board

As we look at what's happened with the Russian attack on the US government and others via Solarwinds, I want to shine a spotlight on a lesson we can apply to threat modeling.
So far, so good.
Going beyond the whiteboard.
A diverse set of experts and advocates for threat modeling are releasing a threat modeling manifesto, modeled after the agile manifesto and focused on values and principles.

Expanding on our distributed class structure.
Compliance isn't Security, oh and something I wrote.
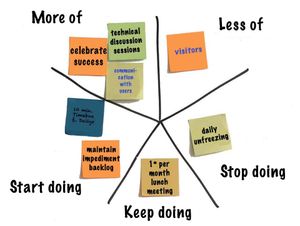
Don't skip this important step.

Inspired by the recent story of Tesla's insider, I'd like to discuss insider threat as it fits into threat modeling.

How to play in person games while maintaining safe distances.

Informal training may work in some cases, but Threat Modeling skills should be passed on through more formal means.

I have something to disclose...
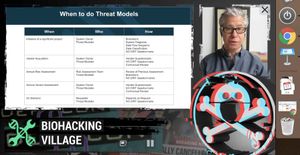
A talk from the Biohacking Village at DefCon brought up a good point.
Not usually one for the video format, I'm expanding my horizons thanks to 2020 being what it is.
I enjoyed being a guest on Software Engineering Radio in this in depth interview.
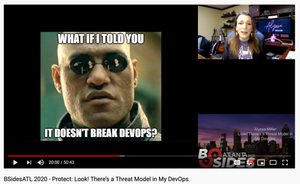
A recent talk by Alyssa Miller focuses on integrating threat modeling in devops.
My thoughts on an interesting blog post discussing how to bring threat modeling into the Scaled Agile Framework.

I'm happy to announce Shostack + Associate's new, first, corporate white paper! It uses Jenga to explain why threat modeling efforts fail so often.
Contextualisation of Data Flow Diagrams for security analysis is a new paper to which I contributed.

For Threat Model Thursday, I want to look at models and modeling in a tremendously high-stakes space: COVID models.
Most of my time, I'm helping organizations develop the skills and discipline to build security in. We give the best advice available, and I recognize that we're early in developing the science around how to build an SDL that works.
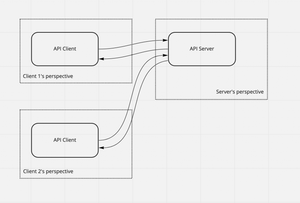
This week's threat model Thursday looks at an academic paper, Security Threat Modeling: Are Data Flow Diagrams Enough? by Laurens Sion and colleagues.

On Linkedin, Peter Dowdall had a very important response to my post on remote threat modeling.
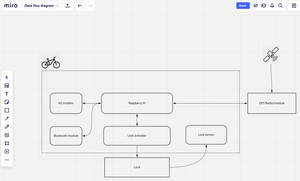
How do we replace the in-person whiteboard sessions essential to Threat Modeling when we are distanced and working remotely?

New training being developed, seeking interest.

This post comes from a conversation I had on Linkedin with Clint Gibler.

While I can't fix things, I can at least make my LinkedIn courses free for a time.

Exploring supply chain threat modeling with Alexa

At Blackhat this summer, I'll be offering threat modeling training at Blackhat. Last year, these sold out quickly, so don't wait!
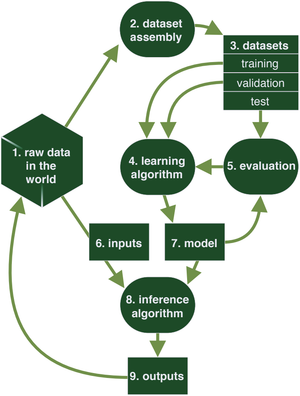
Risk Framework and Machine Learning

My course, “Repudiation in Depth” is now live on Linkedin Learning. This is the fourth course in my Learning Threat Modeling series.
For reasons I can't quite talk about yet, this has been a super busy time, and I look forward to sharing the exciting developments that have kept me occupied.

Have you considered the idea that “Files are Fraught With Peril” lately? Maybe you should...

I joined Caroline Wong on the Humans of Infosec Podcast to discuss The Human Element of Threat Modeling.

Earlier this year, I helped to organize a workshop at Schloss Dagstuhl on Empirical Evaluation of Secure Development Processes. I think the workshop was a tremendous success.

Let's talk CAKED, a threat model for managed attribution.
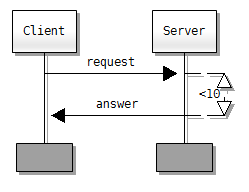
Swim lane diagrams have been formalized in message sequence charts - what that means.
Recently, I've seen four cybersecurity approaches for medical devices, and we can learn by juxtaposing them.

“Includes No Dirt” is a threat modeling approach by William Dogherty and Patrick Curry of Omada Health, and I've been meaning to write about it since it came out.

Don't go into Threat Modeling with this mindset.
Just what the title says.
Just a few things for now

I recently had a chance to speak at the meeting for the Portland, Oregon chapter of OWASP

I'm excited to announce that I'm hitting my STRIDE and Linkedin has released the second course in my in-depth exploration of STRIDE: Tampering.

Threat modeling isn’t one task — its a collection of tasks that build on each other to produce more valuable insights.

I'm excited to be teaming up with Alpha Strike and Limes Security to deliver training in Vienna November 6-8.
Discussing online conflict on the AppSec Podcast
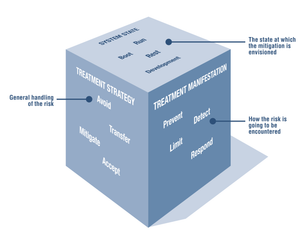
Let’s explore the risks associated with Automated Driving.

Some thoughts on promoting others’ threat modeling work.
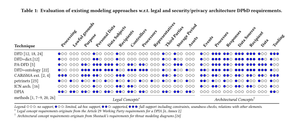
There are a couple of new, short (4-page), interesting papers from a team at KU Leuven discussin the building blocks of threat modeling.
Top 3, from Continuum
Has it been that long already?
RSA has posted a video of my talk, “Threat Modeling in 2019”.
My talks from AppSecCali 2019

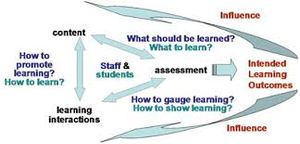
When suggesting that someone needs more training, consider what specific points should be covered.

What comes easily should still be taught and elaborated upon.
Reasons for failure in real-world security

Exploring threat models as code.

My Linkedin Learning course is getting really strong positive feedback. Today, I want to peel back the cover a bit, and talk about how it came to be.
I’m excited to be able to share “Announcement: IriusRisk Threat Modeling Platform 2.0 Released.”

For the last few years, I've been delivering in-person threat modeling training. I've trained groups ranging from 2 to 100 people at a time, and I've done classes as short as a few hours and as long as a week.
Check out my talk from Blackhat 2018
Another podcast, another chance to talk about Threat Modeling

An extended version of Elevation of Privilege, now with Privacy.
[no description provided]
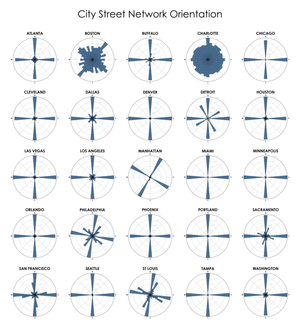
[no description provided]
The slides from my Blackhat talk are now available.

[no description provided]

[no description provided]
[no description provided]
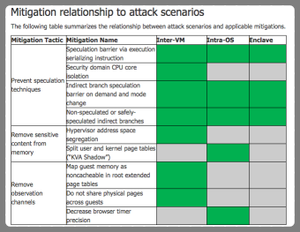
Understanding Google's Post-Spectre threat model
[no description provided]
[no description provided]
[no description provided]

[no description provided]
[no description provided]

[no description provided]

As we head into RSA, I want to hold the technical TM Thursday post, and talk about how we talk to others in our organizations about particular threat models, and how we frame those conversations.
[no description provided]
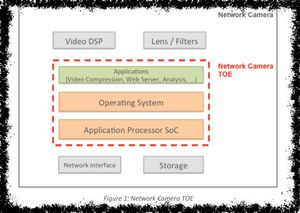
[no description provided]
[no description provided]

[no description provided]
[no description provided]
[no description provided]
[no description provided]
[no description provided]
[no description provided]
[no description provided]
[no description provided]
[no description provided]
[no description provided]

[no description provided]

[no description provided]
[no description provided]
[no description provided]
[no description provided]
[no description provided]

[no description provided]
Recently, I was talking to a friend who wasn't aware that I'm consulting, and so I wanted to share a bit about my new life, consulting!

[no description provided]
[no description provided]

[no description provided]
[no description provided]

[no description provided]
[no description provided]

[no description provided]
[no description provided]
[no description provided]

[no description provided]
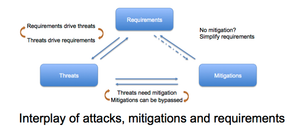
[no description provided]

[no description provided]
[no description provided]

[no description provided]
[no description provided]
[no description provided]
Everyone complains about security, but no one ever... sets boundaries
There are a number of reports out recently, breathlessly presenting their analysis of one threatening group of baddies or another. Most readers should, at most, skim their analysis of the perpetrators. Read on for why.