Miro Threat Modeling Template for EoP
A Miro template for Elevation of Privilege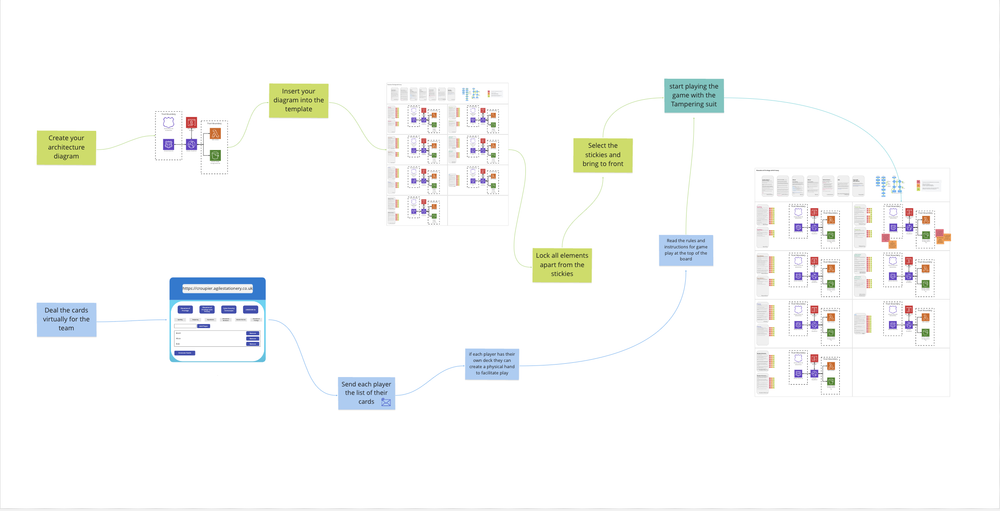
This is a guest post from Brett Crawley
Threat modeling with teams is a process that requires visuals, interaction between team members and discussion and so lends itself to everyone being in a room together. This has been quite hard the last two years. It also doesn't look to be getting any easier, so we should probably get used to it. Here's how I've been doing it with several teams.
To get them started threat modeling their applications, I’ve been using the Elevation of Privilege card game remotely. I've trialed several collaboration tools and methods of play before I came up with the Threat Modeling with EoP Miro Template.
Teams have found this quite helpful in documenting their threat models. They can export them and save them alongside the code in their repo so they have a record of the model for the version of the application they're designing.
I imagine if you're reading this on Adam's site you're already familiar with Elevation of Privilege, so I won't go into the details of play here.
What do you need to play?
You'll need:
- The requirements for what you're building
- An architecture (data flow) diagram which shows your trust boundaries (where ownership or access rights to the data change in the flow)
- A neuro diverse group of people who know what they're building.
How many people and who?
More than one and as many as needed. One pair of eyes is more likely to miss something, so if there are a few of you it works better. When I said a neuro diverse group, by that I mean but don't limit to
- frontend or backend engineers
- someone from QA
- someone from product
- an architect
People in different roles think differently, they may have different context and they/you don't have to be technical (think the door is unlocked, I don't need to be a locksmith to understand that).
How to use the board
The board is split into 3 sections, section 1 contains some instructions for getting setup, section 2 a worked example and section 3 is where the team can model their architecture.
These are the steps to use the board:
- Create an architecture diagram
- Insert your diagram into each of the STRIDE/STRIPED sections of the board
- Lock all elements apart from the stickies
- select all the stickies and "bring to front" from the context menu
- Deal the cards (see below) and share with the players
- Start playing EoP with the 3 of Tampering
- Use the red sticky for the T3 card on the tampering section of the board, add your name and a description of the threat after the number
- You can also add existing mitigations or proposed mitigations with green or orange stickies respectively
- For cards not of the same suite, just grab their sticky and drag them over to the hand you're currently playing.
Finshed the first hand, the winner chooses the next suite and everyone moves to the corresponding section of the board.
Ticket up the threats
If the Jira app is installed in the miro board, you can also create any tickets for mitigation work directly from the board so you don't lose track of them. This might require the administrator to configure the application link but then from the board it's as easy as clicking on a sticky and then clicking the convert to Jira issue button on the context menu as seen below:
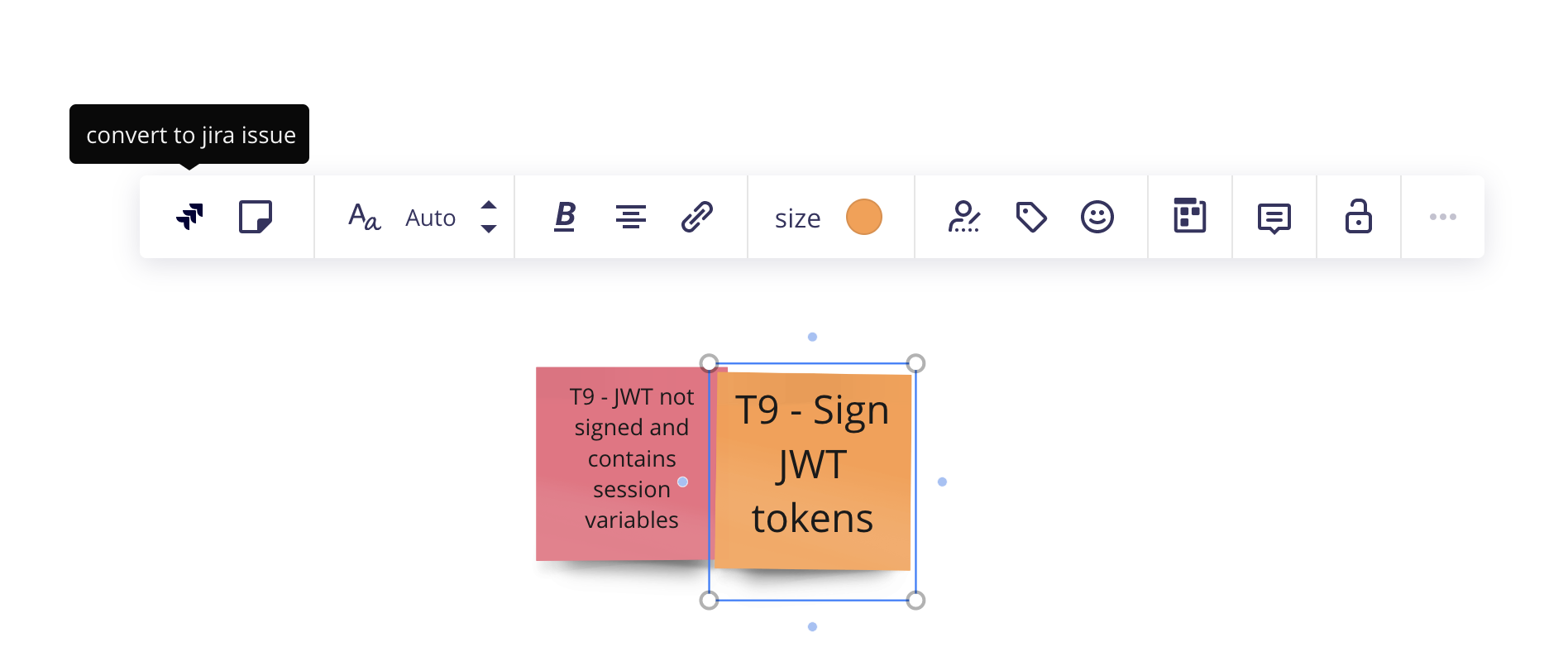
This will open the modal dialog where you can fill out the details of the ticket and then click convert as in the below example:

Dealing the cards virtually
However, if you're playing remotely, you (the facilitator) might also find the croupier app from Agile Stationery useful for dealing the cards. The app allows you to deal for Elevation of Privilege, Elevation of Privilege with Privacy, Cornucopia and LINDDUN Go. I recommend you email each player their respective hand because if you don't finish in one session, I can guarantee in the second session someone won't remember what their cards were.
You can read about some of my other initiatives including the OWASP Application Security Awareness Campaigns and CAPEC-STRIDE Mappings on my blog www.ostering.com
Hope you enjoy it
Author: Brett Crawley, Principal Application Security Engineer @ Mimecast