
Vulnerability Finding: An Inflection Point
LLM-driven vuln finding has reached an inflection

LLM-driven vuln finding has reached an inflection

The 2026 Hackers Almanack is out!

The normalization of deviance, exciting threat modeling news, and a question of do regulatory threats change ‘the threat model’ as much as GPS attacks? Not yet.

Adam will be the featured speaker at the ISC2 Seattle Chapter meeting in February.

NIST 800-218 wants you!
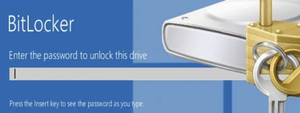
What can the Bitlocker story tell us about risk?
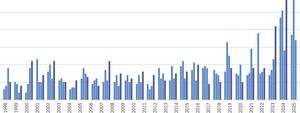
GPS attacks trigger revisiting threat models

In 2026, it’s more important than ever to take control of what you read

Prompted by participants, a few closing thoughts for 2025
Watch Adam's keynote 'Stop Trying to 'Manage Risk'' From OWASP 2025
The first-ever, community-powered report on threat modeling
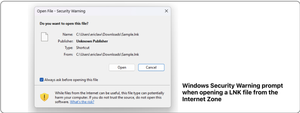
Some dialogs can harm the viewer

Perspective on CISOs as facilitators, a deep dive into the types of diagrams for medical devices, poetry, Chinese LLMs, Chinese drones and Chinese routers. Do any of them contain secrets?

Get in, we’re rebooting the OWASP Threat Modeling project!

Two new versions of our “Publish your threat model” work are now available.

Phil Venables is releasing a masterclass; new guidance from SAFECode, a new paper from JPMorganChase on their tools, how Facebook uses “waves”, a new AI shared responsibility model and more!

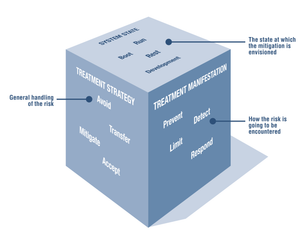
Risk doesn’t do what we hope. We need to talk.

Read up on Adam's New Thing from October

Please vote for the OWASP 2025 board

Watch a masterclass in effective security processes

LLM Insurance is, and will remain, a great source of insurer profits.

The secret service, the CSRB, the CMMC, Sept was pretty busy in government. Plus Apple's Memory Integrity and a nice short paper on prompt-based attacks.

Register for CyberSec Game Challenge 2025!

LLMs will change threat modeling. Will it be for the better?

All the exciting secure by design news from the end of summer

My Usenix Enigma 2025 talk
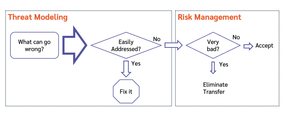
Threat modeling finds threats; risk management helps us deal with the tricky ones.

Lots of fascinating threat model-related advances, new risk management tools, games, and more!

Lots of fascinating threat model-related advances, new risk management tools, games, and more!

Andor teaches us about insider threats
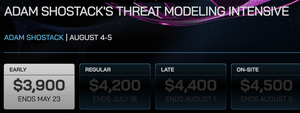

The Cyber Hard Problems report is coming out

Threat modeling. So much threat modeling, and so much more, including foreshadowing of new rules from FDA.

What’s next for the CVE program?

Thoughts on the CVE funding crisis

Big news for LLMs in threat modeling!

A group of us have urged HHS to require better handling of security reports
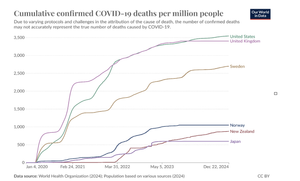
Thinking about Covid, five years on.

New releases from DEF CON, the UK’s NCSC, some entertaining AI news, and more!

Some thoughts on the Voyager Episode ‘Inside Man’

An exciting month, with new threat modeling tools, cool thoughts on STAMP, bounds checking, ADRs and more!

Adam speaking at CERIAS weekly seminar

A virtual feast of appsec!

The goat endures

A virtual feast of appsec!

My talk at JPL

How can we measure the ROI on an awareness month?
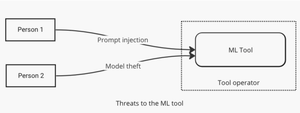
Why do we call them trust boundaries, anyway?

In late 2024, people are being offered a choice of features versus security.

If you say liability three times, it appears!

Some thoughts on 25 years of the CVE program
Time to vote for OWASP leadership

If you say threat modeling three times, it appears!

Secure boot presents questions that should inform the liability conversation

Slides from Adam's talk at the Symposium

The most important stories around threat modeling, appsec and secure by design for August, 2024.
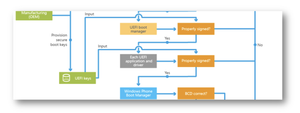
The failure to secure boot keys should be a bigger deal.

A new paper on 'Pandemic Scale Cyber Events

The most important stories around threat modeling, appsec and secure by design for June, 2024.

Cyber Public Health is prompting fascinating conversations

Adam's presentation to a National Academies Panel

Google calls attention to our Cyber Public Health work

Adam will be presenting to a National Academies Panel

The most important stories around threat modeling, appsec and secure by design for June, 2024.

Proud to be an O’Reilly author!

The first workshop on cyber public health was so exciting. Check out the report!
Why is it hard to count lockbit infections?

Adam on the Scale to Zero podcast

Commemorating William Anders

The most important stories around threat modeling, appsec and secure by design for May, 2024.

A less busy month in appsec, AI, and regulation, but still interesting stories

A great threat modeling talk at RSA 2024


What do we need to assess if memory safe langages are 'sufficient'?

Making an LLM forget is harder than it seems

Other people have written about the CSRB report, and I wanted to share their perspectives.

The CSRB has released its report into an intrusion at Microsoft, and...it’s a doozy.


A busy month in appsec, AI, and regulation.

The NVD is in crisis, and so is patch management. It’s time to modernize.

Thoughts on the British Library incident

A busy month in appsec, AI, and regulation.

Solving hallucinations in legal briefs is playing on easy mode —— and still too hard

Adam on The Security Table podcast

A busy month+ in appsec, AI, and regulation.

Comments following the Senate’s CSRB hearing

Adam on Red Queen Dynamics podcast

2024 is bringing lots of AI, and Liability, too

Yet again, attackers surprise us


A threat modeling conference, lots of government appsec guidance, and some updates from Shostack + Associates
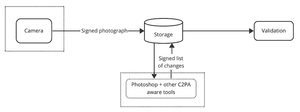
What can we learn from the C2PA security considerations document?
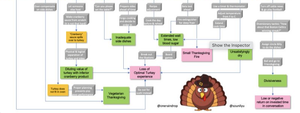
What can we learn from Gunnar Peterson’s Threat Model for Thanksgiving?

Exciting news from the SEC, lots of AI, and lots of threat modeling.

Principles are lovely, but do they lead us to actionable results?

Thinking about adversarial thinking

September was a big month in appsec for both memory safety and policy

The FDA has released their new guidance, which will be broadly impactful.

We can learn a lot from comparing retrospectives

Lots of interesting work in LLMs (again)

Adam featured on ML Sec Ops podcast

Why it’s ok to use the Defcon wifi

The SEC has important new cybersecurity rules

Threat modeling really CAN save you money, just ask Chuck!

Our feedback to CISA is now public

My latest at Dark Reading draws attention to how Microsoft can fix ransomware tomorrow.


Adam's AppSecPNW 2023 keynote

This month runs quite heavy on AI, but the CISA Safe by Design and Default document is going to be important for the next several years.

Tarah Wheeler and Adam write in CFR

Some inferences from layoffs in responsible AI teams

Book signings at RSA, big discounts and more!

Some diagrams to help clarify machine learning threats

Reflecting on the framing of the Threats book

A few tools, some thoughts on injection, some standards, and some of Adam’s appsec news.


Searching my feelings as the audiobook of Threats is released.

This month is all about memory safety, unless you’re a standards group.
The new IEEE S+P is all about usable security.

So many interesting articles from AI to an organizatoion of socio-technical harms, fascinating incident reports about Uber and Circle CI and some history of attack trees.

Adam spoke with Robert Vamosi of The Hacker Mind podcast

Adam joined Paul Roberts on the Conversing Labs podcast

The threats book is in the supply chain, inconsistently.

The live launch party for Threats!

The serious side of the book

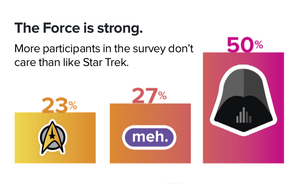
Like the Force, each threat has a light side, and a dark side.

Threat Modeling is the software version of measure twice, cut once.

External changes will be driving appsec in 2023. It’s time to frame the decisions in front of you.

A new paper on how fast, cheap and good can combine into something we usually discount.

Usable security matters
Threats is almost in bookstores

Adam on CSM podcast

Interesting reads this month include signals from the administration, a history of appsec by one of the originals, and a longread from Apple about kernel memory design.

People learning together
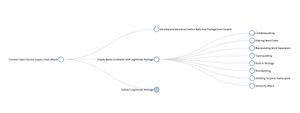
Interesting appsec posts: machine learning, performance, and C4

Our next open course is in just a few weeks!

Our fall course offerings
So excited to share the cover with you
A fun podcast with the ITSP team.

Interesting appsec posts: machine learning, performance, and C4

I'm thrilled this how to guide for standing up new investigations is available.

I'm thrilled the first CSRB report is available.

Interesting appsec posts: from medical devices to bridges.

Threat modeling doesn't need to be big and complex

I've been working with the CyberGreen Institute to develop public health as a way of thinking about cybersecurity.

A collection of interesting appsec posts.

Adam joined Josh and Kurt on the Open Source Security podcast

Exciting news from Adam Shostack on Star Wars Day 2022

A new book on cyberpeace!

The FDA has issued draft guidance for pre-market security

A few lessons from the Mazda radio incident.

The new Cyber Safety Review Board is an opportunity to get better faster.
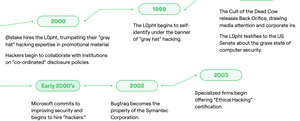
Fascinating history of a transformation in how hackers were seen.

How to threat model medical devices? The FDA has released a playbook!

The definition of insanity is doing the same thing over and over and expecting different results. We can do better, and a major new report explains how.

Time flies and things change... A look back on the growth of this industry.
Arbitrarily powerful software -- applications, operating systems -- is a problem, as is preventing it from running on enterprise systems.

A new article by Steve Bellovin and myself at Lawfare.

The Supreme Court has ruled in the van Buren case, and there's a good summary on the Eff's blog.
The National Science Foundation is looking for information on needs for datasets.
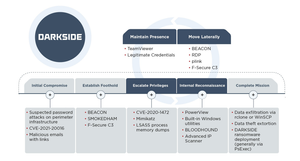
The Colonial Pipeline shutdown story is interesting in all sorts of ways, and I can't delve into all of it.I did want to talk about one small aspect, which is the way responders talk about Darkside.
AppSec Pacific Northwest Conference is a free application security conference that will be held Saturday, June 19th. It is a virtual, online event sponsored by the OWASP chapters of Portland, Vancouver, and Victoria.
Apple has released ‘Device and Data Access when Personal Safety is At Risk’ and I wanted to explore it a bit.
The timing of updates is not coincidental.
It would be trite writing to say it was fun to be on a podcast with Volko Ruhnke and Hadas Cassorla to talk about using games to teach. And while it was, it was really educational and inspirational. I learned from both of them, and I hope you enjoy the podcast as well!
Thoughts on the recent Fireeye Hack and the culture surrounding breaches

Expanding on our distributed class structure.

I recently signed onto the amicus brief on the Van Buren/Computer Fraud and Abuse Act filed by the Electronic Frontier Foundation.
The Internet Society Open Letter Against Lawful Access to Encrypted Data Act was published this morning.

I want to call out some impressive aspects of a report by Proofpoint.
The Sonatype 2020 DevSecOps Community Survey is a really interesting report. Most interesting to me is the importance of effective communication, with both tools and human communication in developer happiness.

There's an interesting new draft, Best Practices for IoT Security: What Does That Even Mean? by Christopher Bellman and Paul C. van Oorschot.
Check out “The Need for Evidence Based Security” by Chris Frenz.

Understanding the way intrusions really happen is a long-standing interest of mine.

While I can't fix things, I can at least make my LinkedIn courses free for a time.

Exploring supply chain threat modeling with Alexa

My course, “Repudiation in Depth” is now live on Linkedin Learning. This is the fourth course in my Learning Threat Modeling series.

A couple big stories in the realm of cryptography that got me excited.

A new game to teach networking and security concepts.
A few tidbits in recent news.

Earlier this year, I helped to organize a workshop at Schloss Dagstuhl on Empirical Evaluation of Secure Development Processes. I think the workshop was a tremendous success.
Recently, I've seen four cybersecurity approaches for medical devices, and we can learn by juxtaposing them.
Sharing for you, bookmarking for me.

I'm excited to announce that I'm hitting my STRIDE and Linkedin has released the second course in my in-depth exploration of STRIDE: Tampering.
Just what the title says

I'm excited to be teaming up with Alpha Strike and Limes Security to deliver training in Vienna November 6-8.
What have we learned and what steps can we take?

A paper at the Workshop on the Economics of Information Security titled “Valuing CyberSecurity Research Datasets” focuses on the value of the IMPACT data sharing platform at DHS, and how the availability of data shapes research.
Let’s explore the risks associated with Automated Driving.
Bruse Marshall has put together a useful comparison of password requirements from OWASP ASVS v3 and v4.

I'm happy to say that some new research by Jay Jacobs, Wade Baker, and myself is now available, thanks to the Global Cyber Alliance.
My newest post over at Dark Reading ponders regulation.

The more we see it, the more we ignore it.
Some points to consider, from Andrew Odlyzko.

Innovation, regulation, and more.
What if we gamified security?

J.E. Gordon’s Structures, or Why Things Don’t Fall Down is a fascinating and accessible book. Why don’t things fall down? It turns out this is a simple question with some very deep answers.

I'm pleased to be able to share work that Shostack + Associates and the Cyentia Institute have been doing for the Global Cyber Alliance.
It's certainly not a silver bullet...
[no description provided]
[no description provided]

[no description provided]

[no description provided]
[no description provided]
[no description provided]
[no description provided]
[no description provided]
[no description provided]
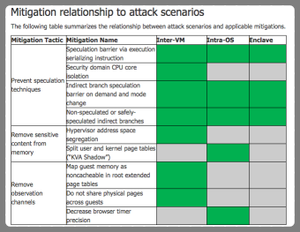
[no description provided]
[no description provided]
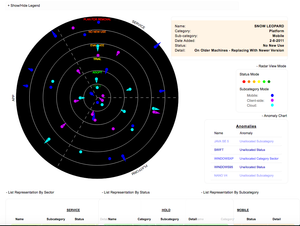
[no description provided]

[no description provided]
[no description provided]
[no description provided]
[no description provided]
[no description provided]
Recently, I was talking to a friend who wasn't aware that I'm consulting, and so I wanted to share a bit about my new life, consulting!
Each of these is long and thought-provoking and worth savoring.

[no description provided]
[no description provided]

[no description provided]
[no description provided]
[no description provided]

[no description provided]
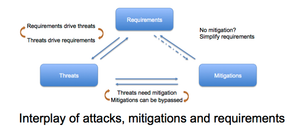
[no description provided]

[no description provided]
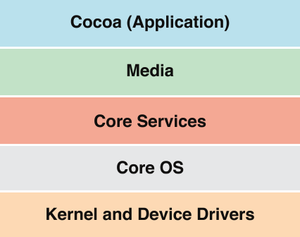
[no description provided]
[no description provided]
[no description provided]
[no description provided]

[no description provided]
[no description provided]
[no description provided]
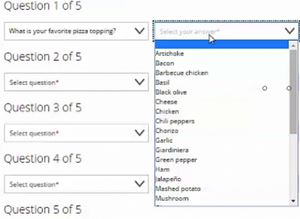
[no description provided]
Everyone complains about security, but no one ever... sets boundaries