
Appsec roundup - Feb 2026
This month's roundup starts with losing oneself, continues with cool new threat modeling tools and applications, and continues into appsec, AI and regulation.

This month's roundup starts with losing oneself, continues with cool new threat modeling tools and applications, and continues into appsec, AI and regulation.

The normalization of deviance, exciting threat modeling news, and a question of do regulatory threats change ‘the threat model’ as much as GPS attacks? Not yet.

Perspective on CISOs as facilitators, a deep dive into the types of diagrams for medical devices, poetry, Chinese LLMs, Chinese drones and Chinese routers. Do any of them contain secrets?

Phil Venables is releasing a masterclass; new guidance from SAFECode, a new paper from JPMorganChase on their tools, how Facebook uses “waves”, a new AI shared responsibility model and more!

Watch a masterclass in effective security processes

Understanding ‘prompt engineering’

LLM Insurance is, and will remain, a great source of insurer profits.

The secret service, the CSRB, the CMMC, Sept was pretty busy in government. Plus Apple's Memory Integrity and a nice short paper on prompt-based attacks.

All the exciting secure by design news from the end of summer

Lots of fascinating threat model-related advances, new risk management tools, games, and more!

Lots of fascinating threat model-related advances, new risk management tools, games, and more!

Threat modeling. So much threat modeling, and so much more, including foreshadowing of new rules from FDA.

What’s next for the CVE program?

Big news for LLMs in threat modeling!
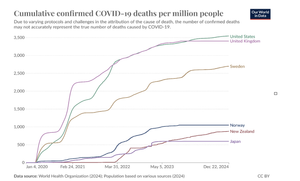
Thinking about Covid, five years on.

New releases from DEF CON, the UK’s NCSC, some entertaining AI news, and more!

Adam was on the CyberTuesday podcast

An exciting month, with new threat modeling tools, cool thoughts on STAMP, bounds checking, ADRs and more!

Adam speaking at CERIAS weekly seminar

Do diagrams leverage the brain in a different way?

A virtual feast of appsec!

A virtual feast of appsec!

In late 2024, people are being offered a choice of features versus security.

If you say liability three times, it appears!
Time to vote for OWASP leadership

If you say threat modeling three times, it appears!

Secure boot presents questions that should inform the liability conversation

The most important stories around threat modeling, appsec and secure by design for August, 2024.
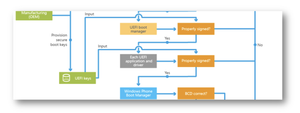
The failure to secure boot keys should be a bigger deal.

The most important stories around threat modeling, appsec and secure by design for June, 2024.

The most important stories around threat modeling, appsec and secure by design for June, 2024.

Adam on the Scale to Zero podcast

Commemorating William Anders

The most important stories around threat modeling, appsec and secure by design for May, 2024.

A less busy month in appsec, AI, and regulation, but still interesting stories

Making an LLM forget is harder than it seems

A busy month in appsec, AI, and regulation.

The NVD is in crisis, and so is patch management. It’s time to modernize.

A busy month in appsec, AI, and regulation.

Solving hallucinations in legal briefs is playing on easy mode —— and still too hard

A busy month+ in appsec, AI, and regulation.

Comments following the Senate’s CSRB hearing
A great new resource for threat modeling

2024 is bringing lots of AI, and Liability, too

A threat modeling conference, lots of government appsec guidance, and some updates from Shostack + Associates
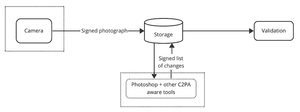
What can we learn from the C2PA security considerations document?
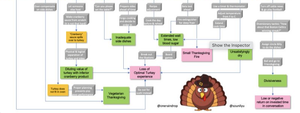
What can we learn from Gunnar Peterson’s Threat Model for Thanksgiving?

Exciting news from the SEC, lots of AI, and lots of threat modeling.

Principles are lovely, but do they lead us to actionable results?

September was a big month in appsec for both memory safety and policy

The FDA has released their new guidance, which will be broadly impactful.

We can learn a lot from comparing retrospectives

Lots of interesting work in LLMs (again)

My latest at Dark Reading draws attention to how Microsoft can fix ransomware tomorrow.


Adam's AppSecPNW 2023 keynote

Phishing behaviors, as observed in the wild.

This month runs quite heavy on AI, but the CISA Safe by Design and Default document is going to be important for the next several years.

Tarah Wheeler and Adam write in CFR

Some inferences from layoffs in responsible AI teams

Book signings at RSA, big discounts and more!

Reflecting on the framing of the Threats book

A few tools, some thoughts on injection, some standards, and some of Adam’s appsec news.

Searching my feelings as the audiobook of Threats is released.

This month is all about memory safety, unless you’re a standards group.
The new IEEE S+P is all about usable security.

Watermarks show us wierd edges of AI work

So many interesting articles from AI to an organizatoion of socio-technical harms, fascinating incident reports about Uber and Circle CI and some history of attack trees.

Adam spoke with Robert Vamosi of The Hacker Mind podcast

Adam joined Paul Roberts on the Conversing Labs podcast

The threats book is in the supply chain, inconsistently.

The live launch party for Threats!

The serious side of the book

Threat Modeling is the software version of measure twice, cut once.

External changes will be driving appsec in 2023. It’s time to frame the decisions in front of you.
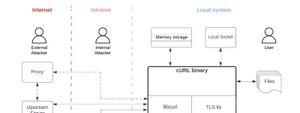
Looking at a threat model for curl, the command line web client.

A new paper on how fast, cheap and good can combine into something we usually discount.
Threat Modeling for UX Designers with Adam Shostack on Heidi Trost's podcast
The OpenAI chatbot is shockingly improved — its capabilities deserve attention.

Text captured from GPT-3
Threats is almost in bookstores

Interesting reads this month include signals from the administration, a history of appsec by one of the originals, and a longread from Apple about kernel memory design.

People learning together
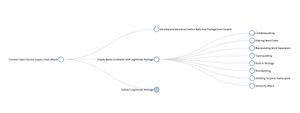
Interesting appsec posts: machine learning, performance, and C4

Our next open course is in just a few weeks!

Our fall course offerings
So excited to share the cover with you
A fun podcast with the ITSP team.

Interesting appsec posts: machine learning, performance, and C4

I'm thrilled this how to guide for standing up new investigations is available.

I'm thrilled the first CSRB report is available.

Interesting appsec posts: from medical devices to bridges.

A collection of interesting appsec posts.

The FDA has issued draft guidance for pre-market security

Threat modeling doesn't need to be a slow, heavyweight activity!
An important webinar by MDIC about the medical device threat modeling playbook is now available!

Adam is delivering the opening keynote for OWASP Global Appsec 2021 with a 25 year restrospective on the history of appsec and a look into its future.

New at Darkreading, a post on NIST and threat modeling

Are you tired of escalations and fights after pen tests find crucial security issues at the last minute? I have a discount code for upcoming threat modeling training that can help!

Are you tired of escalations and fights after pen tests find crucial security issues at the last minute? I have upcoming threat modeling training that can help!

Time flies and things change... A look back on the growth of this industry.

Earlier this week, NIST released a Recommended Minimum Standard for Vendor or Developer Verification of Code. I want to talk about the technical standard overall, the threat modeling component, and the what the standard means now and in the future.
Arbitrarily powerful software -- applications, operating systems -- is a problem, as is preventing it from running on enterprise systems.
AppSec Pacific Northwest Conference is a free application security conference that will be held Saturday, June 19th. It is a virtual, online event sponsored by the OWASP chapters of Portland, Vancouver, and Victoria.
Expanding on the UK Government's ‘The Uk Code of Practice for Consumer IoT Security’ and how it aligns with Threat Modeling.

Dr. Gary McGraw joins the IriusRisk Technical Advisory Board
You may have noticed that my end of the year posts are all science focused. Today, a set of resources on the COVID vaccines.

Expanding on our distributed class structure.

I'm happy to announce Shostack + Associate's new, first, corporate white paper! It uses Jenga to explain why threat modeling efforts fail so often.
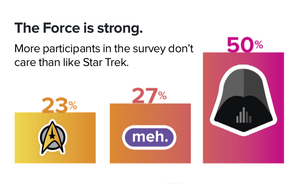
The Sonatype 2020 DevSecOps Community Survey is a really interesting report. Most interesting to me is the importance of effective communication, with both tools and human communication in developer happiness.

There's an interesting new draft, Best Practices for IoT Security: What Does That Even Mean? by Christopher Bellman and Paul C. van Oorschot.
Phil Bull presents an interesting, generally convincing, argument in 'Why you can ignore reviews of scientific code by commercial software developers', with a couple of exceptions.
Most of my time, I'm helping organizations develop the skills and discipline to build security in. We give the best advice available, and I recognize that we're early in developing the science around how to build an SDL that works.
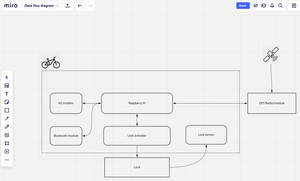
How do we replace the in-person whiteboard sessions essential to Threat Modeling when we are distanced and working remotely?

New training being developed, seeking interest.

Exploring supply chain threat modeling with Alexa

At Blackhat this summer, I'll be offering threat modeling training at Blackhat. Last year, these sold out quickly, so don't wait!
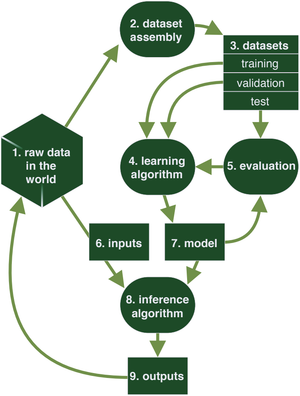
Risk Framework and Machine Learning

My course, “Repudiation in Depth” is now live on Linkedin Learning. This is the fourth course in my Learning Threat Modeling series.

Have you considered the idea that “Files are Fraught With Peril” lately? Maybe you should...
For my first blog post of 2020, I want to look at threat modeling machine learning systems.

Earlier this year, I helped to organize a workshop at Schloss Dagstuhl on Empirical Evaluation of Secure Development Processes. I think the workshop was a tremendous success.

Let's talk CAKED, a threat model for managed attribution.
Recently, I've seen four cybersecurity approaches for medical devices, and we can learn by juxtaposing them.

“Includes No Dirt” is a threat modeling approach by William Dogherty and Patrick Curry of Omada Health, and I've been meaning to write about it since it came out.
Just what the title says.

I'm excited to announce that I'm hitting my STRIDE and Linkedin has released the second course in my in-depth exploration of STRIDE: Tampering.

I'm excited to be teaming up with Alpha Strike and Limes Security to deliver training in Vienna November 6-8.
What have we learned and what steps can we take?
Mitigating the Risk of Software Vulnerabilities by Adopting a Secure Software Development Framework (SSDF) from NIST is open for comment.
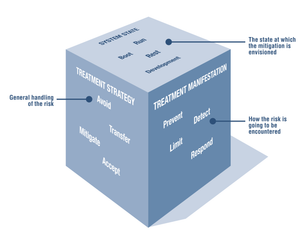
Let’s explore the risks associated with Automated Driving.
The road to mediocre writing is paved with over-simplification and distraction.

Exploring threat models as code.

J.E. Gordon’s Structures, or Why Things Don’t Fall Down is a fascinating and accessible book. Why don’t things fall down? It turns out this is a simple question with some very deep answers.
[no description provided]
[no description provided]

[no description provided]
[no description provided]
[no description provided]
[no description provided]

As we head into RSA, I want to hold the technical TM Thursday post, and talk about how we talk to others in our organizations about particular threat models, and how we frame those conversations.

[no description provided]
[no description provided]

[no description provided]
[no description provided]
[no description provided]
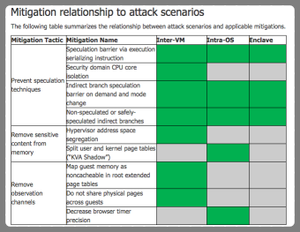
[no description provided]

[no description provided]
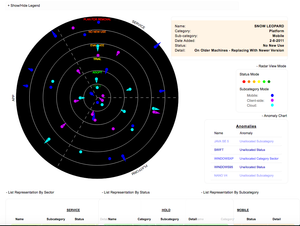
[no description provided]
[no description provided]
[no description provided]
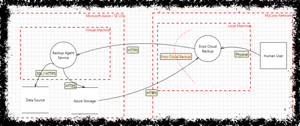
[no description provided]
[no description provided]
[no description provided]
[no description provided]
[no description provided]
Recently, I was talking to a friend who wasn't aware that I'm consulting, and so I wanted to share a bit about my new life, consulting!

[no description provided]
[no description provided]

[no description provided]
[no description provided]
[no description provided]

[no description provided]

[no description provided]
[no description provided]
[no description provided]
[no description provided]

[no description provided]
[no description provided]
[no description provided]