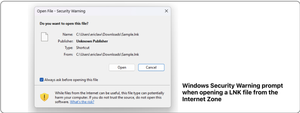
Windows Links and Usable Security
Some dialogs can harm the viewer

Some dialogs can harm the viewer

Accessibility is an ongoing process. Learn about some recent updates to the Shostack + Associates website that increase accessibility and usability.

The psychology of getting started threat modeling

In late 2024, people are being offered a choice of features versus security.

Phishing behaviors, as observed in the wild.
The new IEEE S+P is all about usable security.

A new paper on how fast, cheap and good can combine into something we usually discount.

Usable security matters

Threat modeling doesn't need to be big and complex

Threat modeling doesn't need to be a slow, heavyweight activity!

Making it easier to check feed updates

“It depends on your threat model...”
Going beyond the whiteboard.

How to play in person games while maintaining safe distances.

Informal training may work in some cases, but Threat Modeling skills should be passed on through more formal means.
Contextualisation of Data Flow Diagrams for security analysis is a new paper to which I contributed.
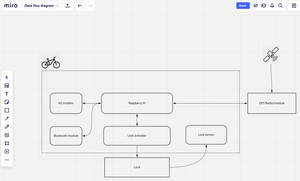
How do we replace the in-person whiteboard sessions essential to Threat Modeling when we are distanced and working remotely?

This post comes from a conversation I had on Linkedin with Clint Gibler.
Bruse Marshall has put together a useful comparison of password requirements from OWASP ASVS v3 and v4.

The more we see it, the more we ignore it.

Some thoughts on promoting others’ threat modeling work.

A resource for those developing games.
What if we gamified security?

A new game from SANS for understanding pen test methodology, tactics, and tools.
[no description provided]
[no description provided]
[no description provided]
Each of these is long and thought-provoking and worth savoring.

[no description provided]

[no description provided]
[no description provided]