
Google’s approach to AI Agents -- Threat Model Thursday
What can we learn from Google’s approach to AI Agent Security

What can we learn from Google’s approach to AI Agent Security
What's wrong with this process?
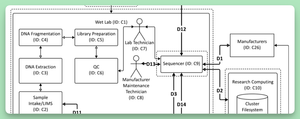
An exciting new sample TM from MITRE

Threat model Thursday, let's dive deep into a detailed approach to using ATT&CK
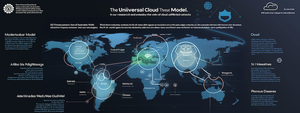
A new universal threat model - what can we learn from it?
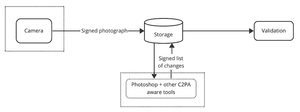
What can we learn from the C2PA security considerations document?
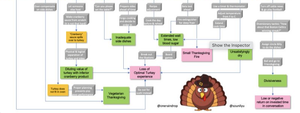
What can we learn from Gunnar Peterson’s Threat Model for Thanksgiving?
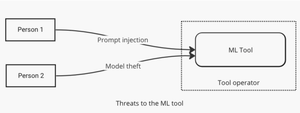
Some diagrams to help clarify machine learning threats

Cumulus is a cloud-oriented version of Elevation of Privilege
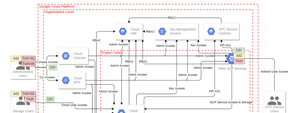
NCC has released a threat model for Google Cloud Platform. What can it teach us?

Threat Modeling is the software version of measure twice, cut once.
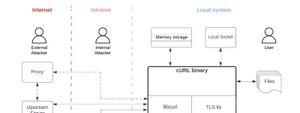
Looking at a threat model for curl, the command line web client.

Earlier this week, NIST released a Recommended Minimum Standard for Vendor or Developer Verification of Code. I want to talk about the technical standard overall, the threat modeling component, and the what the standard means now and in the future.
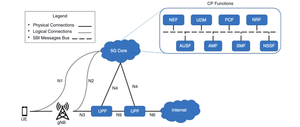
The US Government's lead cybersecurity agencies have released an interesting report, and I wanted to use this for a Threat Model Thursday, where we take a respectful look at threat modeling work products to see what we can learn.
I'm exploring the concept of very fast threat modeling videos.

Threat model Thursday is not just back, but live again!

“It depends on your threat model...”
Expanding on the UK Government's ‘The Uk Code of Practice for Consumer IoT Security’ and how it aligns with Threat Modeling.
A bunch of people recently asked me about Robert Reichel’s post 'How We Threat Model,' and I wanted to use it to pick up on Threat Model Thursdays.
A recent talk by Alyssa Miller focuses on integrating threat modeling in devops.

For Threat Model Thursday, I want to look at models and modeling in a tremendously high-stakes space: COVID models.
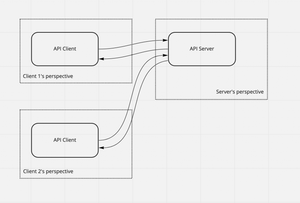
This week's threat model Thursday looks at an academic paper, Security Threat Modeling: Are Data Flow Diagrams Enough? by Laurens Sion and colleagues.

On Linkedin, Peter Dowdall had a very important response to my post on remote threat modeling.

This post comes from a conversation I had on Linkedin with Clint Gibler.

Exploring supply chain threat modeling with Alexa
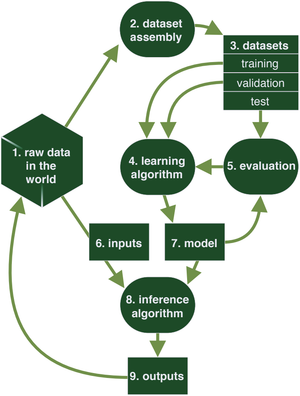
Risk Framework and Machine Learning
For reasons I can't quite talk about yet, this has been a super busy time, and I look forward to sharing the exciting developments that have kept me occupied.

Have you considered the idea that “Files are Fraught With Peril” lately? Maybe you should...

I joined Caroline Wong on the Humans of Infosec Podcast to discuss The Human Element of Threat Modeling.
For my first blog post of 2020, I want to look at threat modeling machine learning systems.

Let's talk CAKED, a threat model for managed attribution.

“Includes No Dirt” is a threat modeling approach by William Dogherty and Patrick Curry of Omada Health, and I've been meaning to write about it since it came out.
There are a couple of new, short (4-page), interesting papers from a team at KU Leuven discussin the building blocks of threat modeling.

[no description provided]
[no description provided]
[no description provided]

[no description provided]
Help me help you.

[no description provided]

[no description provided]
Understanding Google's Post-Spectre threat model
[no description provided]
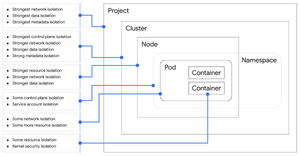
[no description provided]
[no description provided]
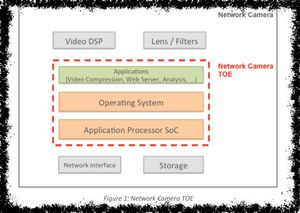
[no description provided]
[no description provided]