Safety and Security in Automated Driving
Let’s explore the risks associated with Automated Driving.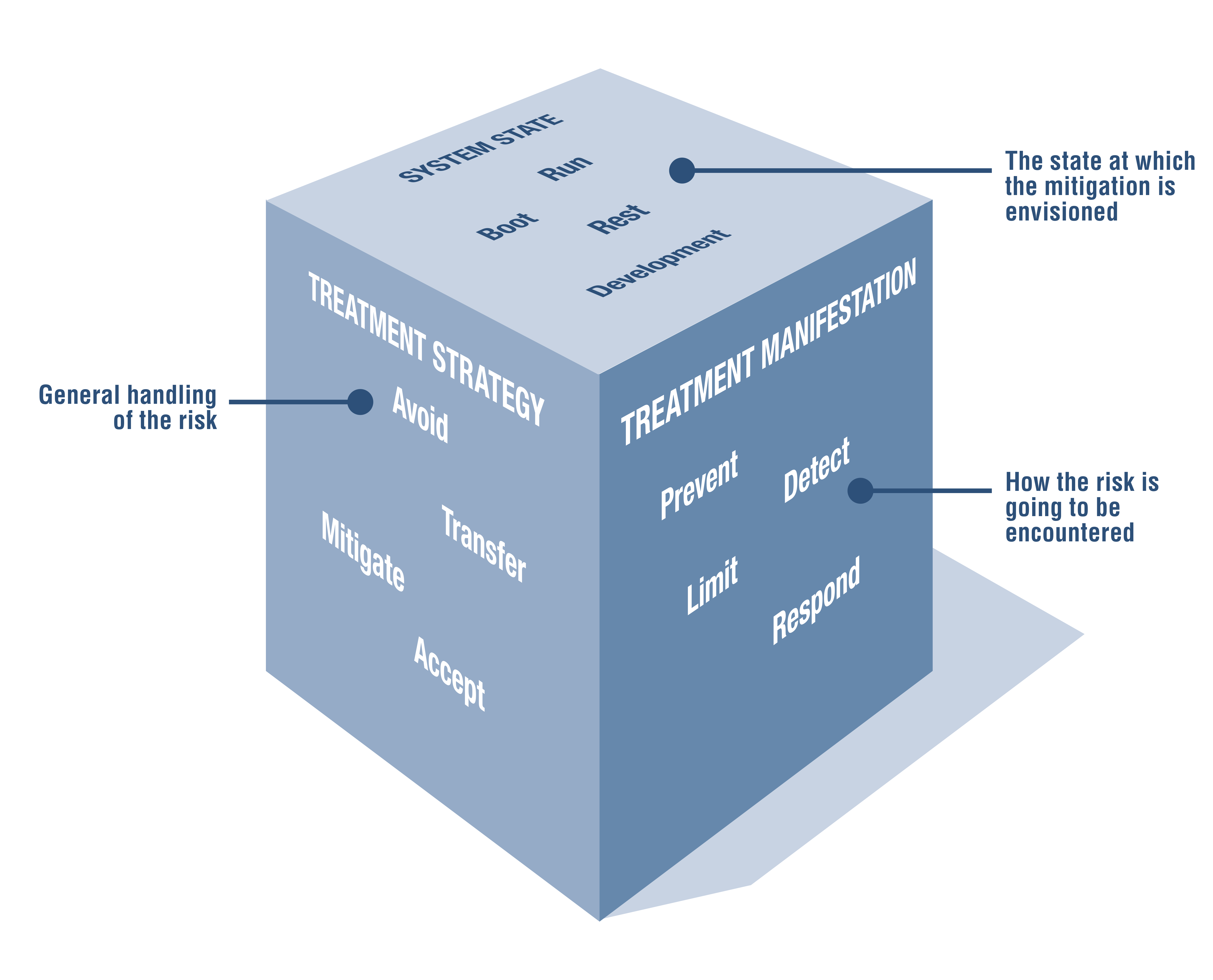
"Safety First For Automated Driving" is a big, over-arching whitepaper from a dozen automotive manufacturers and suppliers.
One way to read it is that those disciplines have strongly developed safety cultures, which generally do not consider cybersecurity problems. This paper is the cybersecurity specialists making the argument that cyber will fit into safety, and how to do so.
In a sense, this white paper captures a strategic threat model. What are we working on? Autonomous vehicles. What can go wrong? Security issues of all types. What are we going to do? Integrate with and extend the existing safety discipline. Give specific threat information and mitigation strategies to component designers.
I find some parts of it surprising. (I would find it more surprising if I were to look at a 150 page document and not find anything surprising.)
Contrary to the commonly used definition of an [minimal risk condition, (MRC)], which describes only a standstill, this publication expands the definition to also include degraded operation and takeovers by the vehicle operator. Final MRCs refer to MRCs that allow complete deactivation of the automated driving system, e.g. standstill or takeover by the vehicle operator.
One of the "minimal risk" maneuvers listed (table 4) is an emergency stop. And while an emergency stop may certainly be a risk minimizing action in some circumstances, describing it as such is surprising, especially when presented in contrast to a "safe stop" maneuver.
It's important to remember that driving is incredibly dangerous. In the United States in 2018, an estimated 40,000 people lost their lives in car crashes, and 4.5 million people were seriously injured. (I've seen elsewhere that a million of those are hospitalized.) A great many of those injuries are caused by either drunk or distracted drivers, and autonomous vehicles could save many lives, even if imperfect.
Which brings me to a part that I really like, which is the 'three dimensions of risk treatment' figure (Figure 8, shown). Words like "risk" and "risk management" encompass a lot, and this figure is a nice side contribution of the paper.
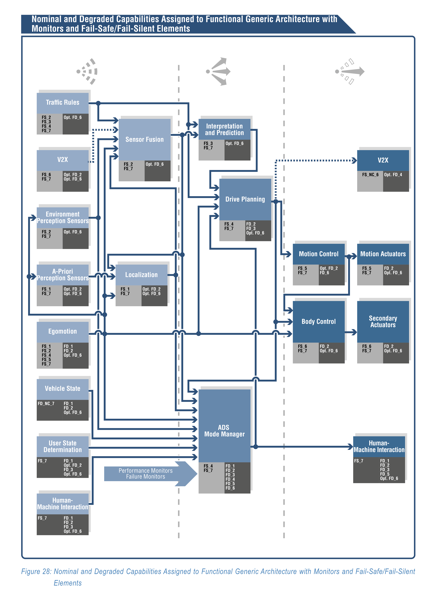
I also like Figure 27 & 28 (shown), showing risks associated with a generic architecture. Having this work available allows systems builders to consider the risks to various components they're working on. Having it available lets us have a conversation about the systematic risks that exist, but also, allows security experts to ask "is this the right set of risks for systems builders to think about?"