
Handling Pandemic-Scale Cyber Threats: Lessons from COVID-19
Emerging research on Cyber Public Health

Emerging research on Cyber Public Health

An important step towards cyber public health

We have a new paper at NDSS

“It depends on your threat model...”
Something to consider
Contextualisation of Data Flow Diagrams for security analysis is a new paper to which I contributed.

There's an interesting new draft, Best Practices for IoT Security: What Does That Even Mean? by Christopher Bellman and Paul C. van Oorschot.
Most of my time, I'm helping organizations develop the skills and discipline to build security in. We give the best advice available, and I recognize that we're early in developing the science around how to build an SDL that works.
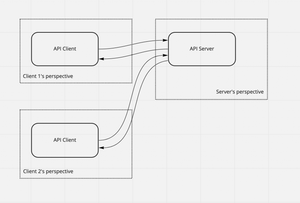
This week's threat model Thursday looks at an academic paper, Security Threat Modeling: Are Data Flow Diagrams Enough? by Laurens Sion and colleagues.

Earlier this year, I helped to organize a workshop at Schloss Dagstuhl on Empirical Evaluation of Secure Development Processes. I think the workshop was a tremendous success.

A paper at the Workshop on the Economics of Information Security titled “Valuing CyberSecurity Research Datasets” focuses on the value of the IMPACT data sharing platform at DHS, and how the availability of data shapes research.
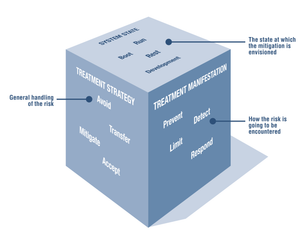
Let’s explore the risks associated with Automated Driving.

The more we see it, the more we ignore it.

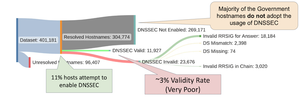
I'm pleased to be able to share work that Shostack + Associates and the Cyentia Institute have been doing for the Global Cyber Alliance.
[no description provided]

[no description provided]
[no description provided]
[no description provided]
[no description provided]

[no description provided]
[no description provided]