Insecurity of Government Infrastructure
We have a new paper at NDSS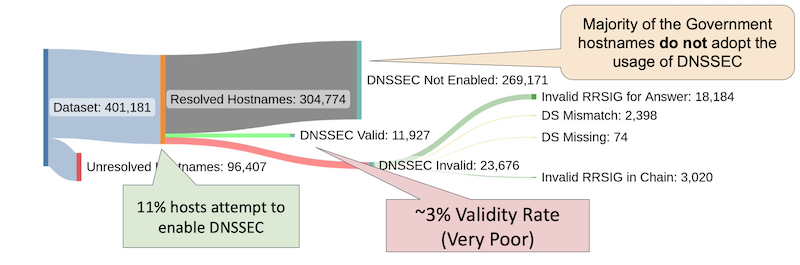
In security, there’s work we do to protect ourselves or our business, and there’s work we do to protect others, or to enable people to securely interact with us. Guess which CISOs tend to prioritize?
Giving society a way to think about, measure, and improve the later is an important value of the “cyber public health” framing. That’s why a group of us, led by Evan Lam and Sudheesh Singanamalla, have a new short paper* in NDSS, “On the (In)Security of Government Web and Mail Infrastructure:”
Abstract: Government web infrastructure is a critical part of today’s Internet and the functioning of society. Citizens’ interactions with digital government infrastructure needs to be secure since they might contain important and sensitive information. These interactions can be through various web applications providing digital public services, or through communication mechanisms such as email. Government websites and mail servers typically form the long tail of today’s Internet and do not appear on large top million Internet datasets making them very understudied. DNS infrastructure forms the center piece for citizens to interact with government services allowing resolution of IP addresses, and enabling email communication and sender policy enforcement between mail service providers. In this poster, due to their inter-dependent nature, we present a comprehensive security evaluation of government web infrastructure covering both web and mail services in addition to understanding the security of the DNS services they rely on. We open source our implementation of the security scanner to the community, invite collaborators to engage with the data periodically scanned, and release the largest public dataset of government hostnames.
* It’s technically accepted as a “poster,” and NDSS lets you post two page explainers with those posters.