Medical Device Threat Modeling Webinar
An important webinar by MDIC about the medical device threat modeling playbook is now available!

An important webinar by MDIC about the medical device threat modeling playbook is now available!

The definition of insanity is doing the same thing over and over and expecting different results. We can do better, and a major new report explains how.

Adam is delivering the opening keynote for OWASP Global Appsec 2021 with a 25 year restrospective on the history of appsec and a look into its future.
A video interview by OWASP leader Vandana Verma, on the topic of breaking into threat modeling.

Tremendous training opportunities in threat modeling and other topics at Appsec Global 2021
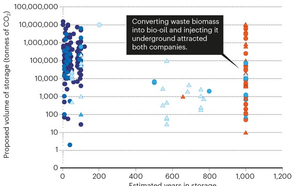
What happened when Microsoft tried to buy climate abatements

We learn while we're having fun. Some takeaways from a recent play to learn session.

New at Darkreading, a post on NIST and threat modeling

Andrew Stewart has an excellent new book, A Vulnerable System.

The World's Shortest Threat Modeling Video series continues with .. what can go wrong?

Are you tired of escalations and fights after pen tests find crucial security issues at the last minute? I have a discount code for upcoming threat modeling training that can help!

Making it easier to check feed updates
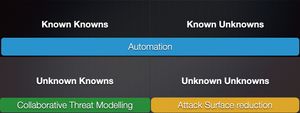
Let me call your attention to a new post by Irene Michlin, “Where Threat Modelling fits in the matrix?” (with a few comments on why it matters).

Are you tired of escalations and fights after pen tests find crucial security issues at the last minute? I have upcoming threat modeling training that can help!

Time flies and things change... A look back on the growth of this industry.