Sketching to Answer 'What are we working on?'
The latest in the World's Shortest Threat Modeling Videos.

The latest in the World's Shortest Threat Modeling Videos.
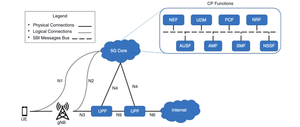
The US Government's lead cybersecurity agencies have released an interesting report, and I wanted to use this for a Threat Model Thursday, where we take a respectful look at threat modeling work products to see what we can learn.

At Blackhat USA, I'll be teaching Applied Threat Modeling.
The second video in my 60 second series!

Thoughts on the new federal holiday, Juneteenth
I'm exploring the concept of very fast threat modeling videos.

You know what's not in my threat model? A meteor hitting a volcano... And that's ok!
Arbitrarily powerful software -- applications, operating systems -- is a problem, as is preventing it from running on enterprise systems.

A new article by Steve Bellovin and myself at Lawfare.

The Supreme Court has ruled in the van Buren case, and there's a good summary on the Eff's blog.

People sometimes ask me about my recording setup, and I wanted to share some thoughts about recording good learning content.

Adam Shostack's review of the book Practical Cybersecurity Architecture

Threat model Thursday is not just back, but live again!
The National Science Foundation is looking for information on needs for datasets.
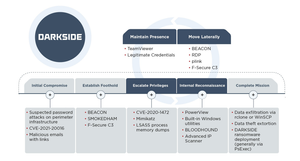
The Colonial Pipeline shutdown story is interesting in all sorts of ways, and I can't delve into all of it.I did want to talk about one small aspect, which is the way responders talk about Darkside.