Threat Model Thursday: Data Flow Diagrams
This week's threat model Thursday looks at an academic paper, Security Threat Modeling: Are Data Flow Diagrams Enough? by Laurens Sion and colleagues.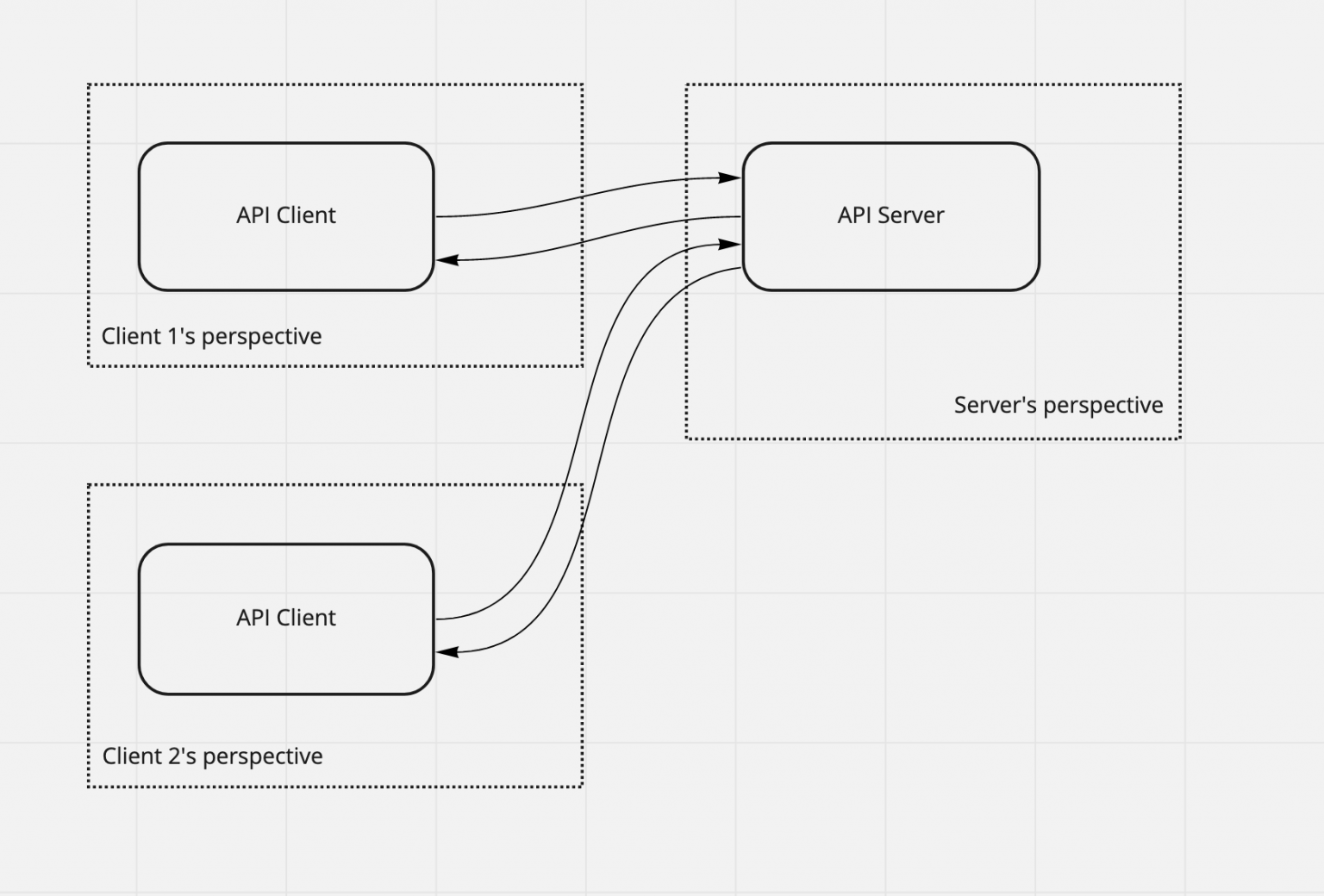
This week's threat model Thursday looks at an academic paper, Security Threat Modeling: Are Data Flow Diagrams Enough? by Laurens Sion and colleagues. The short (4 page), readable paper looks at the strengths and weaknesses of forms of DFDs, and what we might achieve with variations on the form and different investments of effort. I take issue with the framing of 'enough', as if there's a single definition of enough that's enough for all of us, but that's the authors' choice. Anyone who thinks deeply about how threat modeling works will benefit from reading the paper and thinking about how those tradeoffs work for their organization.
Also interesting is their discussion of the meaning of a trust boundary. They lay out three meanings:
- Levels of trust
- Assumptions of attacker capabilities
- Deployment information
I think there's a 4th meaning of trust boundary, which is a trust boundary indicates separation of principals by some control, and the boundary is instantiated by the control. All of these are facets of the same thing, but that doesn't tell us what a trust boundary is, it tells us what we mean by it or what it indicates.
Another way of saying that is the boundary is 'the place' where the principals interact, but consider my diagram with an API endpoint and two boundaries. From the perspective of the client, the clients are mutually mistrustful, but does the server care about that distinction? Perhaps it does - the server probably wants to keep client data segregated. The clients want the same, but after it's crossed the boundary, by definition, that's a matter of trust (or encryption).
So two takeaways for today: first, go read "Are Data Flow Diagrams Enough?" Second, please tell me what a trust boundary means to you.
Proper, academic citation: Laurens Sion, Koen Yskout, Dimitri Van Landuyt, Alexander van den Berghe, Wouter Joosen, Security Threat Modeling: Are Data Flow Diagrams Enough?, 1st International Workshop on Engineering and Cybersecurity of Critical Systems (EnCyCriS), In EEE/ACM 42nd International Conference on Software Engineering Workshops (ICSEW’20), Seoul, South Korea, May 23-29, 2020.