
What do you get the person who has everything?
The best gift for 2023

The best gift for 2023

Pointer to Adam’s latest Darkreading article

Usable security matters

Books that I read in the fourth quater that are worth your time include several about safety with lessons for cybersecurity
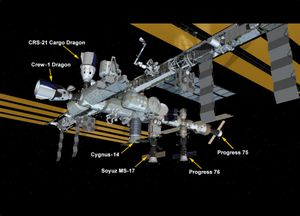
Interesting space news, including ISS and 3d printed engines
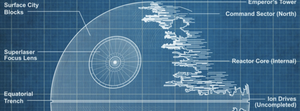
Legal commentary on the Second Death Star Project
Threat Modeling for UX Designers with Adam Shostack on Heidi Trost's podcast
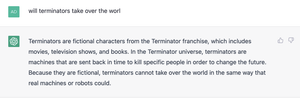
The OpenAI chatbot is shockingly improved — its capabilities deserve attention.

Text captured from GPT-3
Threats is almost in bookstores

Adam on CSM podcast

Interesting reads this month include signals from the administration, a history of appsec by one of the originals, and a longread from Apple about kernel memory design.

People learning together
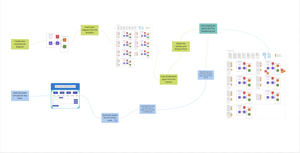
A Miro template for Elevation of Privilege

Oh my gosh, the boot camps are back!