
Shostack + Friends Blog
Recent Blog Posts, Page 17


The Hacker Mind
Adam spoke with Robert Vamosi of The Hacker Mind podcast

Not all developers can be Jedi
Adam joined Paul Roberts on the Conversing Labs podcast

Threats, To The Supply Chain
The threats book is in the supply chain, inconsistently.

Friday Star Wars: Presidents Daily Brief
The return of the (my) Friday Star Wars posts

Threats Book Launch Party
The live launch party for Threats!

Threats Book is Complete
The serious side of the book

Threats: The Table of Contents
Like the Force, each threat has a light side, and a dark side.

Threat Modeling is Measure Twice, Cut Once
Threat Modeling is the software version of measure twice, cut once.

The Appsec Landscape in 2023
External changes will be driving appsec in 2023. It’s time to frame the decisions in front of you.

The Last 747
Thoughts on the last 747, and engineering culture.
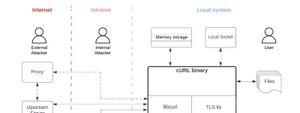
Threat Model Thursday: curl
Looking at a threat model for curl, the command line web client.

Fast, Cheap and Good, Redux
A new paper on how fast, cheap and good can combine into something we usually discount.

More on GPT-3 and threat modeling
More thoughts about AI and threat modeling

Gavle Goat
A straw goat that has not been burned.