
Cyber Hard Problems Report
The Cyber Hard Problems report is coming out

The Cyber Hard Problems report is coming out

BlackHat invites human factors work

My talk at JPL

A few thoughts from a clickbait headline

BlackHat invites human factors work

An interesting discovery, hidden in Leonardo da Vinci's notebooks

A beautiful comparison site that allows you to see how the Webb telescope compares to Hubble.

I've been working with the CyberGreen Institute to develop public health as a way of thinking about cybersecurity.

Life will find a way!
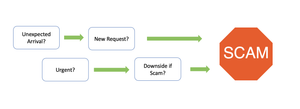
Roger Grimes has an exciting new model of scams that's going to transform how we teach people ot defend against them.

The Evergreen line has had another ship run aground.

The definition of insanity is doing the same thing over and over and expecting different results. We can do better, and a major new report explains how.
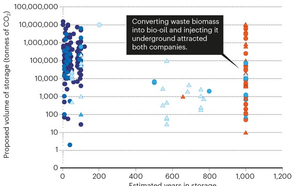
What happened when Microsoft tried to buy climate abatements

The pandemic gives us a chance to evaluate AI tools...you'll be shocked to discover how they did.

A new article by Steve Bellovin and myself at Lawfare.
The National Science Foundation is looking for information on needs for datasets.
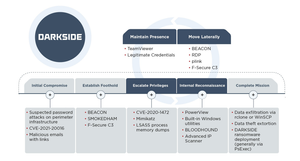
The Colonial Pipeline shutdown story is interesting in all sorts of ways, and I can't delve into all of it.I did want to talk about one small aspect, which is the way responders talk about Darkside.
If everyone agrees on what we should do, why do we seem incapable of doing it?
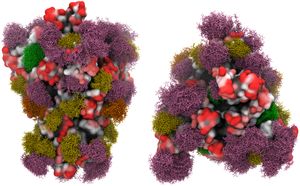
You may have noticed that my end of the year posts are all science focused. Today, a set of resources on the COVID vaccines.

It's easy to forget that the Lunar Reconnaissance Orbiter has been circling the moon for nearly a dozen years..

Check out this close-up of a dinosaur tail preserved in amber!
The video of my Distinguished Lecture at Ruhr University Bochum is now online, and I've got reference to share as well.
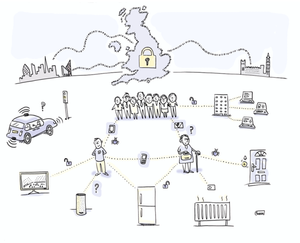
A recent post from Helen L. of the UK’s NCSC, A sociotechnical approach to cyber security, shares the context of socio-technical approaches.
Phil Bull presents an interesting, generally convincing, argument in 'Why you can ignore reviews of scientific code by commercial software developers', with a couple of exceptions.

Understanding the way intrusions really happen is a long-standing interest of mine.

As a member of the BlackHat Review Board, I would love to see more work on Human Factors presented there.

Earlier this year, I helped to organize a workshop at Schloss Dagstuhl on Empirical Evaluation of Secure Development Processes. I think the workshop was a tremendous success.
Just what the title says.

Threat modeling isn’t one task — its a collection of tasks that build on each other to produce more valuable insights.

A paper at the Workshop on the Economics of Information Security titled “Valuing CyberSecurity Research Datasets” focuses on the value of the IMPACT data sharing platform at DHS, and how the availability of data shapes research.

The more we see it, the more we ignore it.
[no description provided]

Near misses are an important source of information for avoiding accidents, and it's a shame we don't use them in cybersecurity.
[no description provided]
[no description provided]
[no description provided]
[no description provided]
[no description provided]

[no description provided]
[no description provided]