Testing Building Blocks
There are a couple of new, short (4-page), interesting papers from a team at KU Leuven discussin the building blocks of threat modeling.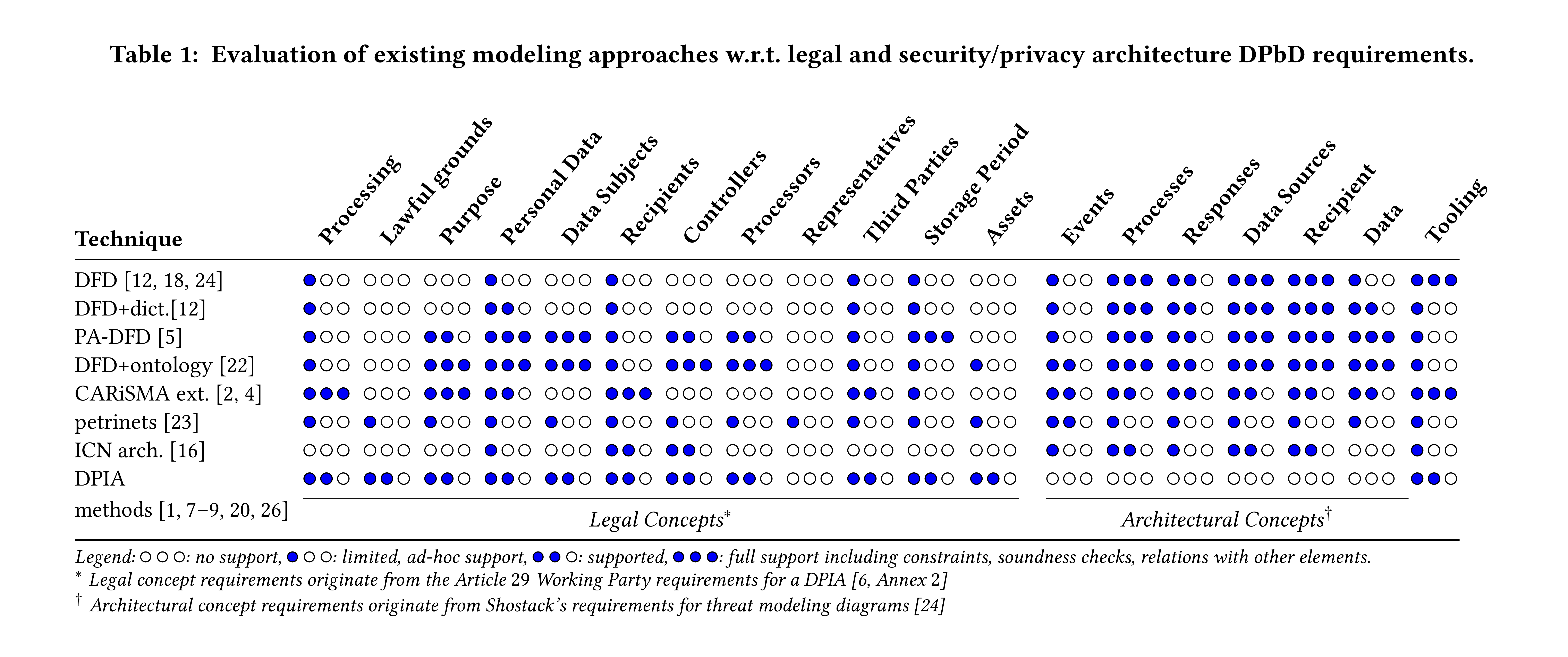
There are a couple of new, short (4-page), interesting papers from a team at KU Leuven including:
- Knowledge is Power: Systematic Reuse of Privacy Knowledge for Threat Elicitation
- A Comparison of System Description Models for Data Protection by Design
What makes these interesting is that they are digging into better-formed building blocks of threat modeling, comparing them to requirements, and analyzing how they stack up.
The work is centered on threat modeling for privacy and data protection, but what they look at includes STRIDE, CAPEC and CWE. What makes this interesting is not just the results of the comparison, but that they compare and contrast between techniques (DFD variants vs CARiSMA extended; STRIDE vs CAPEC or OWASP). Comparing building blocks at a granular level allows us to ask the question "what went wrong in that threat modeling project" and tweak one part of it, rather than throwing out threat modeling, or trying to train people in an entire method.