Threat Model In My Devops
A recent talk by Alyssa Miller focuses on integrating threat modeling in devops.

A recent talk by Alyssa Miller focuses on integrating threat modeling in devops.
My thoughts on an interesting blog post discussing how to bring threat modeling into the Scaled Agile Framework.
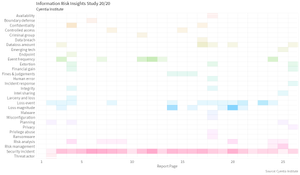
I'm excited to see that they're Re-introducing the Cyentia Research Library, with cool (new?) features like an RSS feed. There are over 1,000 corporate research reports with data that companies paid to collect, massage, and release in a way they felt would be helpful to the rest of the world.

Juneteenth is the celebration of the end of slavery in the US. We need more holidays that celebrate freedom. Freedom isn't always comfortable or easy, but it is the precondition to the pursuit of happiness.

I'm happy to announce Shostack + Associate's new, first, corporate white paper! It uses Jenga to explain why threat modeling efforts fail so often.

I want to call out some impressive aspects of a report by Proofpoint.
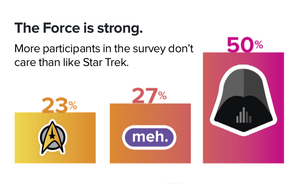
The Sonatype 2020 DevSecOps Community Survey is a really interesting report. Most interesting to me is the importance of effective communication, with both tools and human communication in developer happiness.
Contextualisation of Data Flow Diagrams for security analysis is a new paper to which I contributed.

There's an interesting new draft, Best Practices for IoT Security: What Does That Even Mean? by Christopher Bellman and Paul C. van Oorschot.
Check out “The Need for Evidence Based Security” by Chris Frenz.
I generally try to stay on technical topics, because my understanding is that's what readers want. But events are overwhelming and I believe that not speaking out is now a political choice.
As I built out my home studio to record videos for my distributed classes, I was lucky enough to be able to find an in-stock HDMI capture card, but those are harder and harder to find. As it turns out, you may be able to avoid the need for that with a mix of apps.
Phil Bull presents an interesting, generally convincing, argument in 'Why you can ignore reviews of scientific code by commercial software developers', with a couple of exceptions.

Understanding the way intrusions really happen is a long-standing interest of mine.

For Threat Model Thursday, I want to look at models and modeling in a tremendously high-stakes space: COVID models.