The Grimes Model of Scams
Roger Grimes has an exciting new model of scams that's going to transform how we teach people ot defend against them.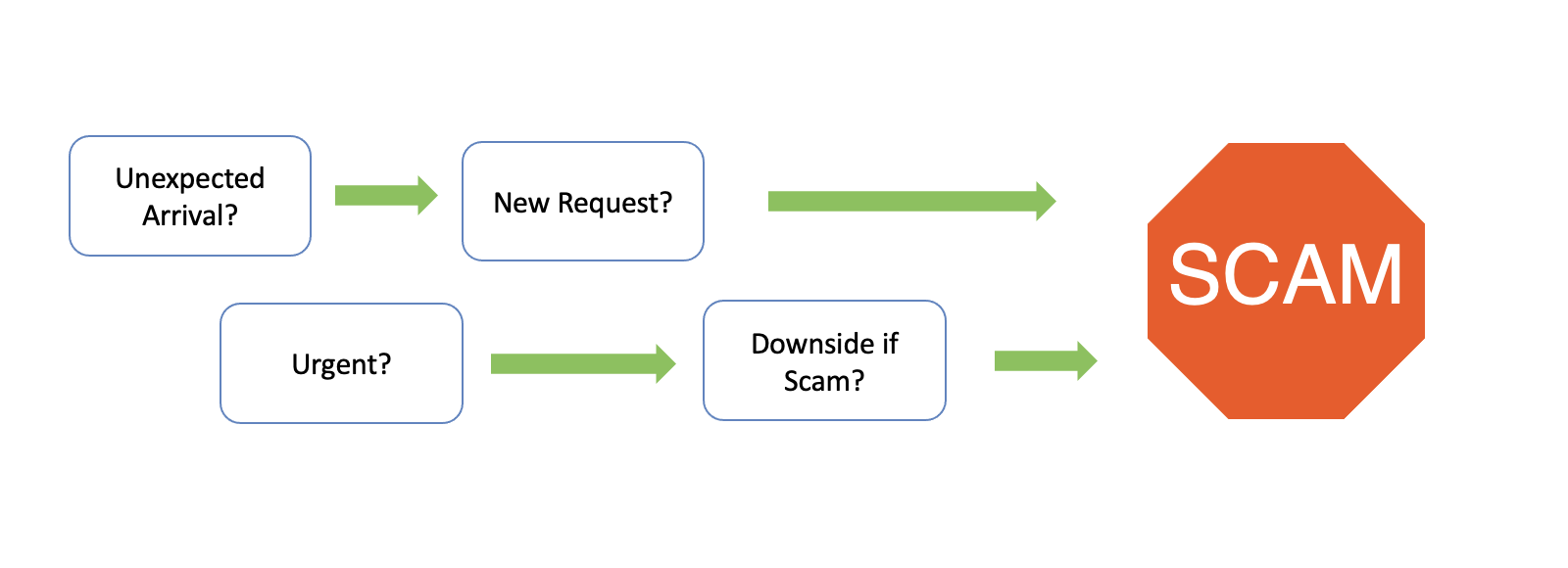
Over the years, I've had the opportunity to look at scams and cons and how they translate to technical systems. And while scams are fascinating, technical cybersecurity tends to treat them with even more disdain than social engineering concerns. The scorn and victim blaming can be something to see.
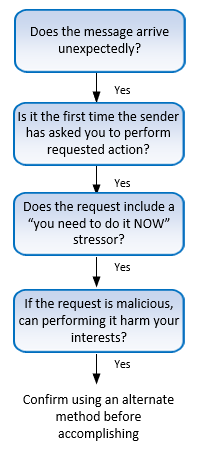
So I was pretty excited to see an article from Roger Grimes, Traits of Most Scams. This is a model of threats, a way of answering the question "what can go wrong?" It's largely analagous to STRIDE in that sense. It has a couple of nice properties to it. They include simplicity and longevity. The simplicity is somewhat self-evident. The longevity is a result of the properties being hard for scammers to avoid: an unexpected message, urgency, a downside to you, and a thing you haven't been asked to do before.
It's likely that the message is unexpected - if it's expected, the scammer has either spent a long time on preparation ("the long con"). It's urgent because a lot of the infrastructure scammers use will get taken down, and it's also likely that you'll notice that something is odd or too good to be true. The downside to you is the reason the scammer is scamming, and it's new to you because if they've asked you, you're probably more wary. Of course, there are romance scams and advance fee frauds where the requests cascade, but there was a first request in the chain.
Similarly, the "confirm using an alternate method" is what we called "a path to safety." (I think this was originally pointed out by Ellen Cram Kowalczyk, who said taking control of a situation is a powerful technique as you travel. Scammers initiate contact with you - the random person you ask for help is less likely to be involved.) Visiting a bookmark, using a search engine, calling the number on the back of your card all get you to that alternate channel and out of the scammer's space.