Threat Modeling and Logins
Authentication is more frustrating to your customers when you don’t threat model.
Recently, I was opening a new bank account. The bank unexpectedly sent me a temporary password to sign up, and when I did, the temporary password had expired. So it sent me another, this time warning me it was only going to last ten minutes. But then, after I went to reset the password, the bank emailed me a one time code. Which is a fine practice, and brings me to the question: Why expire the first passwords at all? They’re checking live access to the email account with the one time code. An attacker who has access to my email has what they need to get in. Why make it harder? The passwords I chose are unlikely to be better than “toz*!Iikc@mpP8gD” (with a password manager they’ll be equally good, but most people don’t use a password manager.)
I have to admit, I’m literally baffled by what’s going on here. I’ve tried to find a way in which this process makes sense, and I can’t. What I think is happening is cargo cult security. They (or their auditors) see parts of these patterns in use, and say “that seems helpful.” But they haven’t broken down what the various parts do, and so they pile layers of security on. To the extent that only impacts them, that’s fine, but here it wastes my time, and especially my attention as I wait for the next wasted message to make it out of theirtems to mine. I can’t do anything useful as I wait.
A related example (and I’ll explain how they relate) comes from a friend, who used the “press one to get called back” that his bank offers. When he did, they sent him a text message to authenticate him, and it says “DO NOT share this access code with anyone. Only enter it on the bank mobile app or website.”
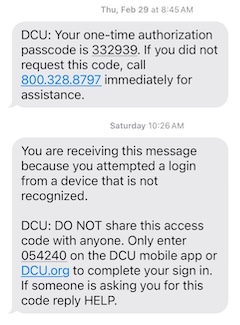
You’ll be shocked to hear that the customer support rep, who was calling him, asked for the code. The design of that bank’s systems involved one team setting an expectation that another of their teams violated.
People can only learn when there’s consistency in what they’re told. If you’re literally told “do A” and “don’t do A”, there are only two lessons you can learn:
- I cannot make heads or tails of this and that’s ok
- I cannot make heads or tails of this and I should go elsewhere.
Ok, technically there’s more lessons, which are in this blog post, but you know what I mean...
One way to deal with this situation of mutual authentication is telling the customer “When we call you back, our rep will say “sleeping zebras in purple mountains” so you know it’s us. You could put that phrase in the text (“You can also tell someone who says ‘sleeping zebras...’”) The phrase is short enough to be memorable, it’s subject to fuzzy matching by people (“Was it supposed to be zebras? I remember it was mostly that.”) This is imperfect, but better than what they’re doing. A list of 1000 each verbs, nouns and adjectives gives you enough randomness when a person is answering phonels. By the way, I don’t mean to pick on DCU, nor do I feel obligated to redact the image.
The common thread is a lack of effective threat modeling. Threat modeling gives you:
- A way to identify specific threats and mitigations
- A process for that identification and tracking that management can rely on
- A defined ritual to help it happen
- A time for consideration and coordination
You can learn the need for a way to authenticate the bank to the customer with a ceremony diagram. You can analyze it for spoofing threats, and asking who knows what at each stage. You can also get to other answers, and threat modeling gives you a frame in which to assess which ones might be right for your situation.
Happier customers. Less frustration. Fewer customer support calls. Please: threat model your authentication processes.
Update 1: After I wrote this post, I learned that ING Bank has a tool, “Check the Call” that displays who’s calling you within their app. Good for them! Both my solution and the one from ING are vulnerable to a monkey in the middle attack, where the attacker is calling you and the bank at the same time. But they’re still a big improvement, requiring two attackers and a live connection.
Update 2: See also the followup post.
Image by midjourney: “an animated or anime or pixar officious clown carefully checking someones identity documents. They have an ID card in one hand and a checklist nearby. You can see the other person who looks exhausted, on the far side of a desk. The clown is bureaucratic, ineffective and slow. --ar 8:3”