The Updates Must Go Through
The timing of updates is not coincidental.On Monday, the Department of Justice announced that it had cleaned malware ("webshells") off of hundreds of infected mail systems running Microsoft Exchange. Microsoft has been trying to get folks to apply critical security patches to address a problem that's being actively exploited.
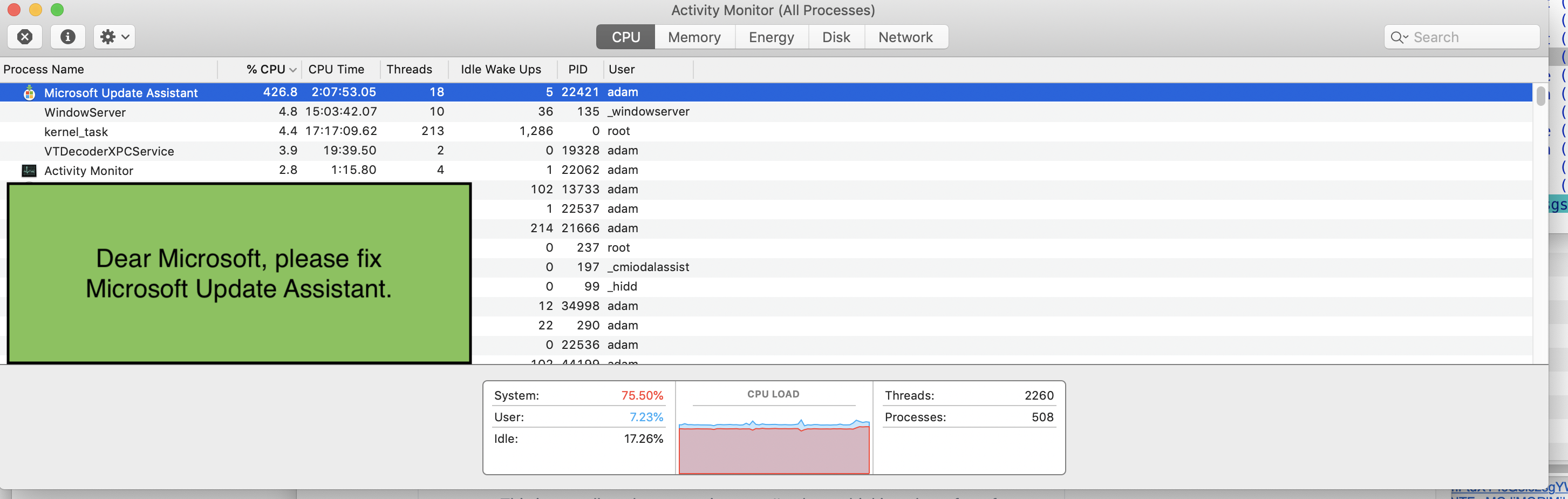
A few minutes ago, I posted a this screencapture of Microsoft's autoupdater going haywire on my Mac. The two stories are intimately related to people not wanting to roll patches. This is a story I've been watching closely for twenty years or so. (For example, see our Timing the Application of Security Patches for Optimal Uptime, Usenix Lisa 2002).
There were some improvements along the way. In 2004, Microsoft shipped the Blaster removal tool to remove a virulent worm. That worm had code which targeted Windowsupdate.com with a denial of service attack. I remember being in a meeting where Jason Garms described the history of that tool, and how it morphed into the Malicious Software Removal Tool (MSRT). Controversial at the time, Apple now has it's own variant of that built quietly into MacOS, and we'll come back to MSRT vs DoJ.
Microsoft evolved Windows Update into Microsoft Update, with a promise that you'd only need one updater. Today, I have at least three on this computer: Microsoft Update, which seems to update itself more than anything else, but also manages updates for Office. Teams has its own updater, as does Skype. Probably other tools do as well, because Microsoft seems to have taken its eye off the ball of flawless updating.
Low flaw, low impact updating is possible; observe Chrome and Firefox, with their restore after restart. (Admittedly, a browser is easier than an operating system, and I have many brickbrats for Cupertino there, too.)
When your updates are not reliable and low impact, people avoid them.
When Jason talked about Blaster, he said "We made the decision that Windowsupdate was going to be the last Microsoft property standing. We can only get back if we can clean this thing up."
Cleaning this thing up is what the DoJ did last week. So, why DoJ, not Microsoft? Probably because some mix of: MSRT runs on fewer corporate machines than consumer ones, hesitancy to set a precedent that the DoJ can order Microsoft to execute code on machines, the DoJ's desire to flex a new precedential muscle. There may have been other factors. And when I say "hesitancy," I know at least a few folks still at Microsoft who would have shown up with baseball bats to help people see reason in the face of that idea.
And really, we do not want companies being told by governments to run code on people's computers. Updates are too important to the health of the digital world to see them disrupted. Trust in those updates is easily lost and hard to regain. Leaving Microsoft out of it was the right thing to do. I just wish that team would improve the quality of the update pathway, because that's also the right thing to do.