
Car Safety Factoids
A few thoughts from a clickbait headline

A few thoughts from a clickbait headline

Some thoughts on 25 years of the CVE program

The first workshop on cyber public health was so exciting. Check out the report!

Other people have written about the CSRB report, and I wanted to share their perspectives.

The CSRB has released its report into an intrusion at Microsoft, and...it’s a doozy.

Thoughts on the British Library incident

We can learn a lot from comparing retrospectives

I'm thrilled this how to guide for standing up new investigations is available.

I'm thrilled the first CSRB report is available.

The new Cyber Safety Review Board is an opportunity to get better faster.
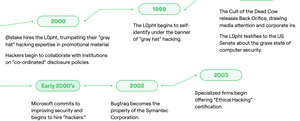
Fascinating history of a transformation in how hackers were seen.

So there's some good news and some bad news in this story: 'Too Bad, Zuck: Just 4% of U.S. iPhone Users Let Apps Track Them After iOS Update'.
Expanding on the UK Government's ‘The Uk Code of Practice for Consumer IoT Security’ and how it aligns with Threat Modeling.
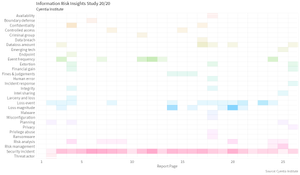
I'm excited to see that they're Re-introducing the Cyentia Research Library, with cool (new?) features like an RSS feed. There are over 1,000 corporate research reports with data that companies paid to collect, massage, and release in a way they felt would be helpful to the rest of the world.

I want to call out some impressive aspects of a report by Proofpoint.
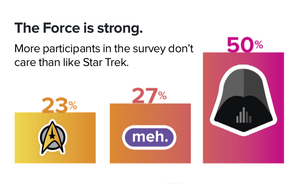
The Sonatype 2020 DevSecOps Community Survey is a really interesting report. Most interesting to me is the importance of effective communication, with both tools and human communication in developer happiness.

Understanding the way intrusions really happen is a long-standing interest of mine.
Most of my time, I'm helping organizations develop the skills and discipline to build security in. We give the best advice available, and I recognize that we're early in developing the science around how to build an SDL that works.
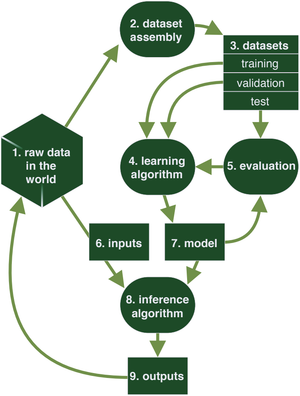
Risk Framework and Machine Learning

Earlier this year, I helped to organize a workshop at Schloss Dagstuhl on Empirical Evaluation of Secure Development Processes. I think the workshop was a tremendous success.

A paper at the Workshop on the Economics of Information Security titled “Valuing CyberSecurity Research Datasets” focuses on the value of the IMPACT data sharing platform at DHS, and how the availability of data shapes research.

I'm happy to say that some new research by Jay Jacobs, Wade Baker, and myself is now available, thanks to the Global Cyber Alliance.

The House Oversight Committee has released a scathing report on Equifax...

I'm pleased to be able to share work that Shostack + Associates and the Cyentia Institute have been doing for the Global Cyber Alliance.
[no description provided]
[no description provided]

[no description provided]
[no description provided]
There are a number of reports out recently, breathlessly presenting their analysis of one threatening group of baddies or another. Most readers should, at most, skim their analysis of the perpetrators. Read on for why.