A Black Hat Sneak Preview (Part 1 of ?)
Alex and I will be on a panel, A Black Hat Vulnerability Risk Assessment, at this year’s Black Hat. We’ll be discussing the need to perform a risk assessment of vulnerabilities as you become aware of them in a deeper context then just looking at the CVSS scores. Things to consider are what compensating controls may be in place, the value of the data being protected and how likely is it that an? attack will happen and how often it will be successful.
Alex and I have developed a model, The Mortman/Hutton Probabilistic Model of Exploit Use, that we hope will assist with this risk assessment. We’ll be posting portions of the white paper we wrote for Black Hat over the next couple of weeks, as well as updates to the model as it evolves in response to our own research and your feedback. We’d love to hear what you think.
Part 1, ” Background: On Technology Adoption” is below:
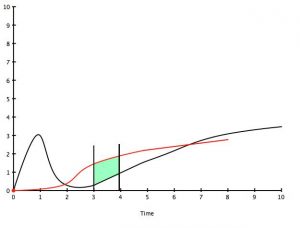
Tipping Point v2
Using the pre-supposition that the classic Gartner Hype Cycle curve (above) represents a real model for rate of technology adoption and is applicable to the use of an exploit, the Mortman/Hutton model is an attempt to understand the factors that will “drive the curve”. So if we can say that the Gartner Hype Cycle represents the evolution of vulnerabilities with regards to a particular technology or a portion of that technology, then the first peak is what we see when researchers and/or miscreants first start examining that technology. This represents the low hanging fruit, that was either missed or deemed acceptable risk by the producers. After the initial burst of research, activity generally tapers off for a while based on a number of factors (that can be represented in part by the model). Once the research community gets more comfortable with the technology and has enough time to really start digging into its guts, more exploits start to appear and often they are more damaging or harder to fix. Additionally as you move along the curve, exploits start appearing in Metsploit and similar toolsets and eventually into tools that script kiddies and analysts can use.
If the black line represents activity around a vulnerability/exploit, then the red line represents the deployment of that same technology within organizations. Where the two lines overlap is when things start to get interesting, In the example above, the organization already has a heavy deployment of that technology when the second upswing of vulnerability research has started. As such the shaded area represents the tipping point where the CSO should seriously start worrying about the risk of vulnerabilities within there technology. Similarly, if the overlap is in a different place then a different rsik assessmment will result.
The Mortman/Hutton model attempts to help security professionals understand what will make exploit code “move” from 2 to 3 on the X axis. It is an examination of the factors that drive the probable creation and use of exploit tools.
Hello, Alex (and Dave) –
A legend for the graph would be helpful.
The x axis appears to have something to do with time, but the unit of measurement is not stated. I have no idea what the y axis could mean.
(Low hanging fruit = 3 ??? at timepoint = 0.9 ???)
Also, for those of us not “in-the-know”, some background on the Gartner Hype cycle curve, and why you think it reasonable as a starting point, would be helpful. (I assume that there are data to back this up, hence the shape of the lines.)
Patrick
Patrick,
Here’s more info on the “Gartner Hype Cycle.
The shape of the curves will vary from technology to technology, so this is more of a gedankenexperiment if you will. We can generate more specific curves but that requires gathering data which we will be discussing in greater detail in later posts. Additionally, Adam has posted regularly here and at Emergent Chaos on the need for more data (not to mention the book).
Thanks, Dave –
FYI – we met briefly at Source Boston, and I trained in FAIR with Alex and Jack Jones last December in Columbus.
Best,
Patrick
Dave/Alex –
I have looked at the link on hype cycles, and even though, as a general set of observations about technology adoption, it rings somewhat true with my own experience, I don’t really see how one could consider it a methodology.
Since no data are provided to explain the specific shape of the lines, it requires something of an act of faith for me to buy into it.
Perhaps Gartner has data on its web site, but unfortunately, in order to learn more, you have to be a Gartner subscriber, which I am not.
Hopefully, you and Alex will be able to provide something convincing to help me out.
Patrick
Hi Patrick!
I wouldn’t spend much time just on the hype cycle. We’re using it as a presupposition, yes, but really only to say that *something* causes *some* sort or adoption curve. Not having the $$$ to find out the hows & whys of the Gartner HC, but it being fairly well known, we decided to use it as a reference point.
Hi, Alex –
Fair enough – I look forward to part 2.