Threat Advisory: GPS Attacks [SA-26-01]
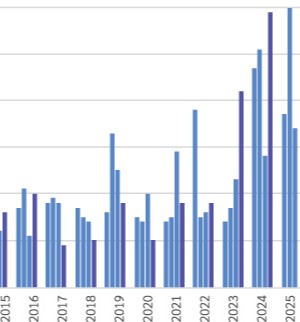
The dramatic increase in credible reports of GPS attacks, combined with geographic spread and the decreasing cost of hardware for the attack, indicate a change in the threat landscape. If your company or organization relies on GPS for location or time information, you should update your threat models.




